Introduction
When your data travels over the public internet, it’s exposed to risks—interception, breaches, and unauthorized access. Azure Private Endpoints solve this by letting you connect to services like Storage or SQL through a private IP address in your Virtual Network. This keeps your data off the public internet and within Microsoft’s secure network.
In this guide, we’ll explain how Private Endpoints work, why they matter for privacy, and how to set them up.
What Are Azure Private Endpoints?
Azure Private Endpoints act like secret tunnels to your Azure services (Storage, SQL DB, etc.). They assign a private IP address from your Virtual Network (VNet) to a specific resource, so traffic bypasses the public internet entirely. Instead of cruising the chaotic highway, your data rides Microsoft’s private backbone network secure, fast, and snoop-free.
Why You’ll Love Private Endpoints
- Locked-Down Security: No public IP? No problem. Your service stays hidden from internet randos.
- Traffic Privacy: Data travels exclusively over Microsoft’s network—no detours through sketchy public routes.
- Granular Control: Pair with Network Security Groups (NSGs) or User-Defined Routes (UDRs) to tighten access.
- Compliance Friendly: Meet regulations like GDPR/HIPAA without breaking a sweat.
- Smooth Sailing: Reduced latency and fewer hops mean better performance.
Private vs. Public Endpoints: The Showdown
| Aspect | Public Endpoints | Private Endpoints |
|---|---|---|
| Access | Open to the internet (yikes!). | Restricted to your VNet or VPN/ExpressRoute. |
| Routing | Public internet (hello, latency!). | Microsoft’s backbone (fast lane!). |
| DNS Resolution | Public IP via public DNS. | Private IP via Azure Private DNS Zones. |
| Security | Needs extra firewalls/NSGs. | Built-in isolation; internet? Never heard of it. |
| Compliance | Possible, but requires heavy lifting. | Easier to audit and lock down. |
TL;DR: Public endpoints = convenience; Private endpoints = security + control.
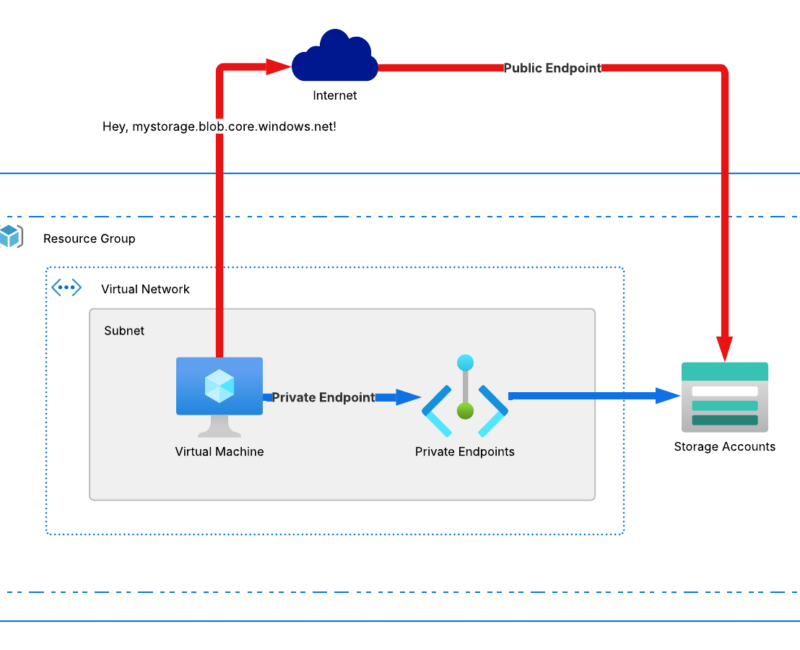
How Traffic Flows: Public vs. Private
Public Endpoint Flow
- Client Request: “Hey,
mystorage.blob.core.windows.net!” - DNS: Resolves to a public IP.
- Routing: Traffic zigzags through the public internet (risky!).
- Access: Hits the service’s public endpoint hope your firewalls are awake!
Private Endpoint Flow
- Client Request: Same FQDN, but from your VNet.
- DNS Magic: Private DNS Zone maps it to a VNet-private IP.
- Routing: Stays entirely on Microsoft’s backbone (no public roads!).
- Access: Direct line to your service via the private IP.
Lab Time: Secure Azure Storage with a Private Endpoint
What You’ll Need:
- An Azure subscription.
- Basic Azure Portal skills.
- A VNet (we’ll create one!).
Step 1: Build Your Virtual Network
- Create a Resource Group:
- Name:
RG-PrivateEndpointLab(region: pick your favorite).
- Name:
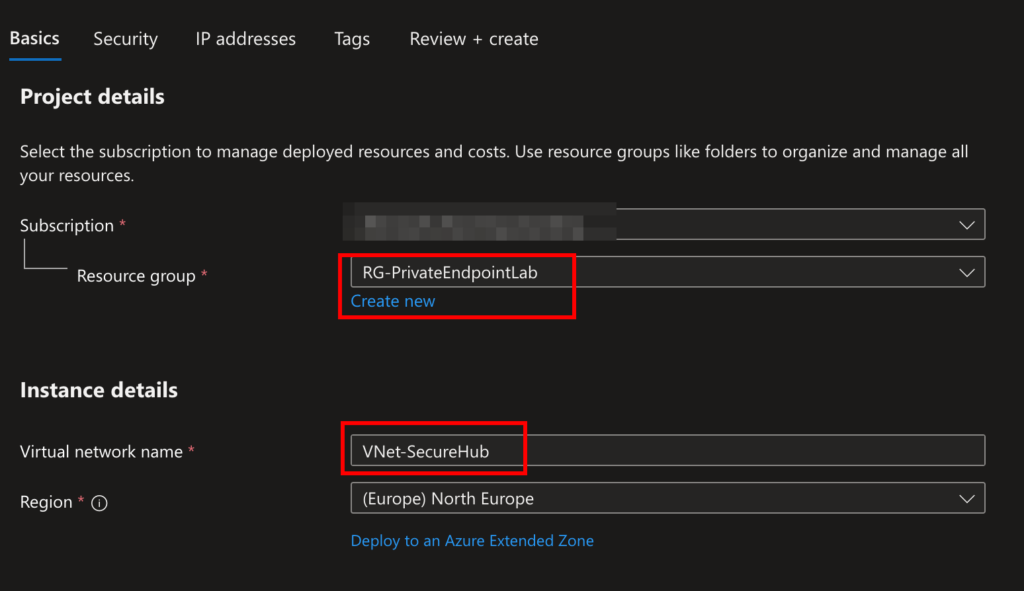
- Create a VNet:
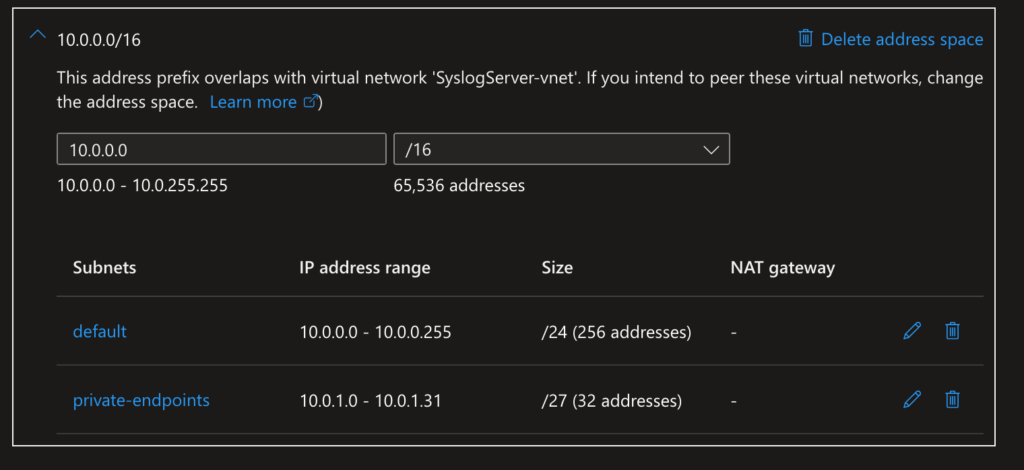
- Name:
VNet-SecureHub, address space:10.0.0.0/16. - Subnets:
default:10.0.0.0/24(for general resources).private-endpoints:10.0.1.0/27(dedicated to Private Endpoints).
- Name:
Step 2: Deploy a Storage Account
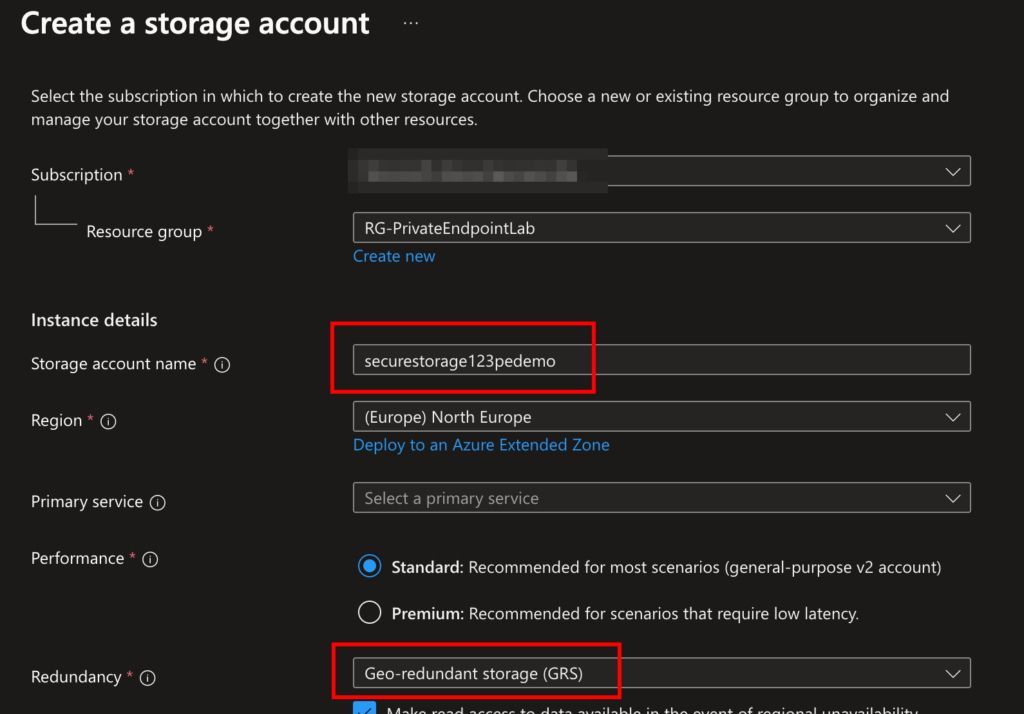
- Go to Storage Accounts → + Create.
- Name:
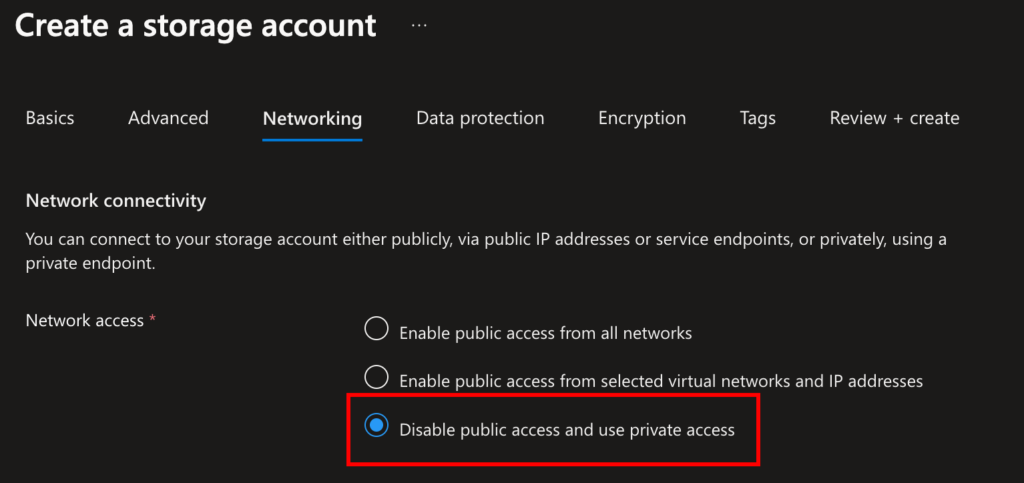
securestorage123pedemo, General-purpose v2. - Under Networking, disable public access (we’re going private!).
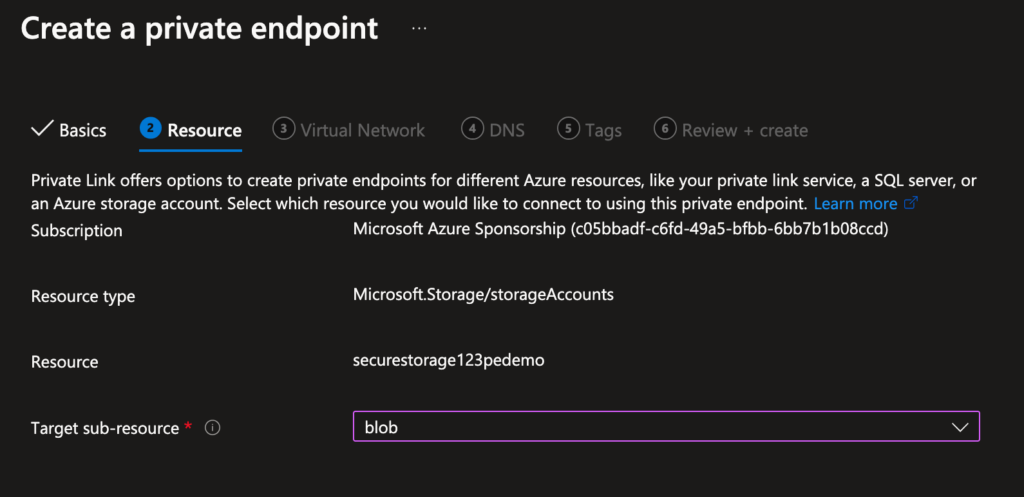
Step 3: Link a Private Endpoint
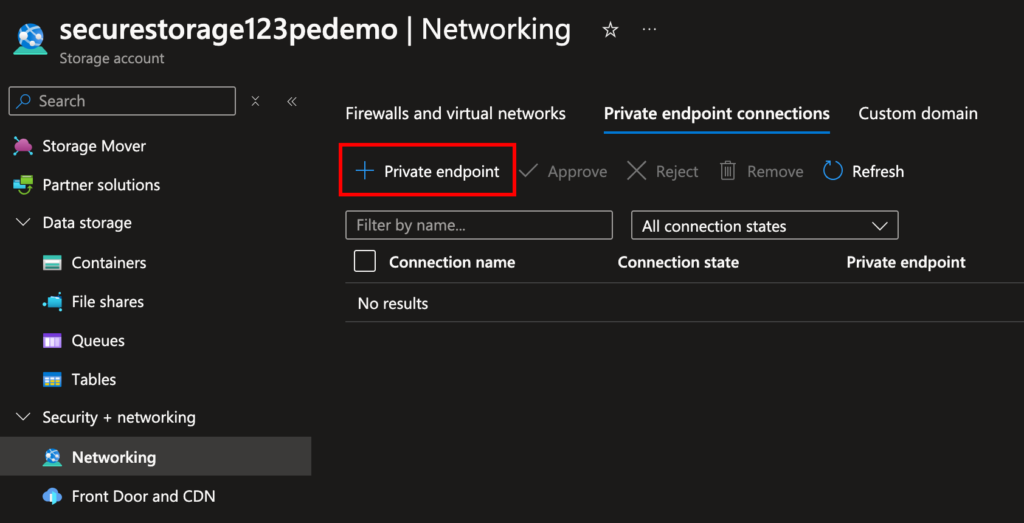
- In your Storage Account → Networking → Private Endpoint Connections → + Private Endpoint.
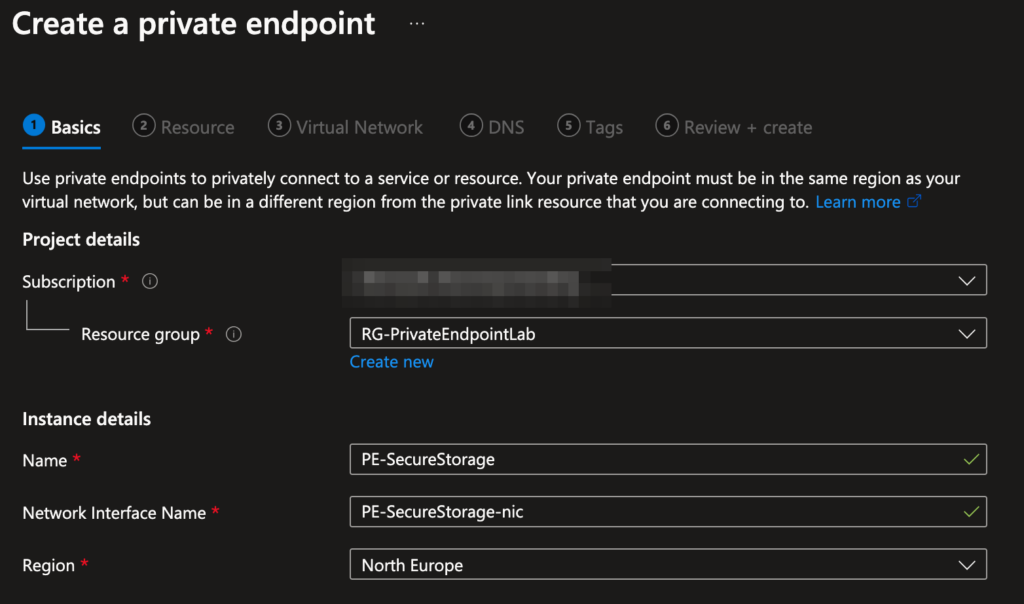
- Name:
PE-SecureStorage. - Resource: Select your storage account.
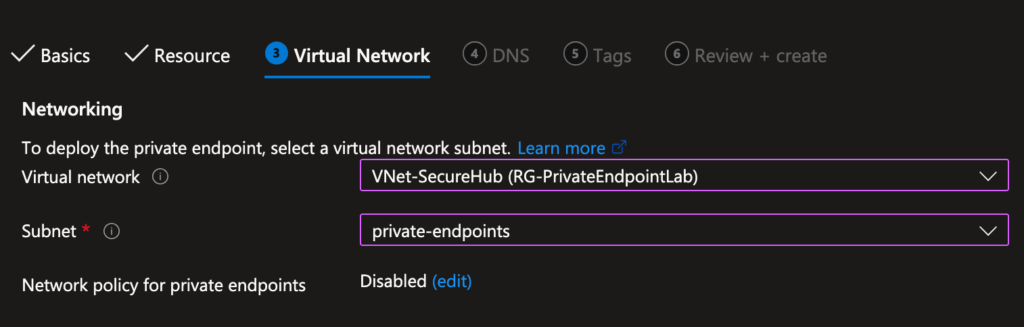
- Network: Attach to
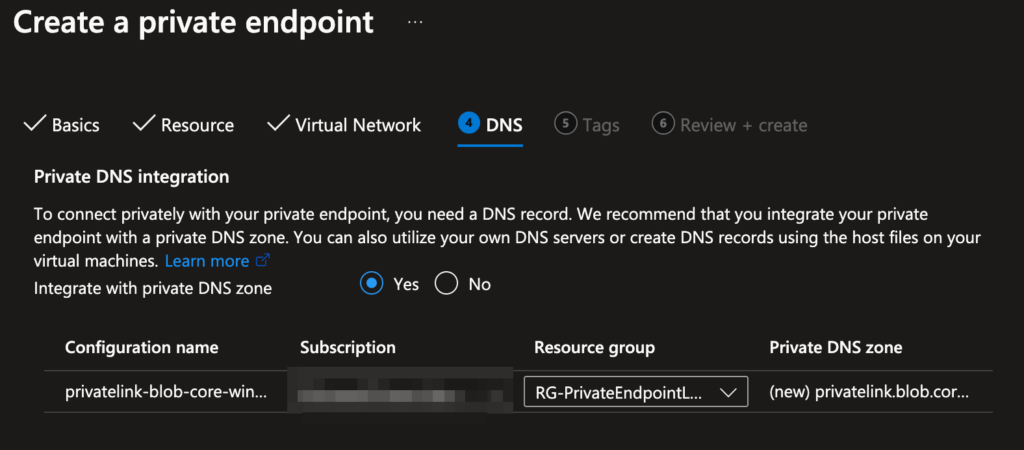
VNet-SecureHubandprivate-endpointssubnet. - DNS: Check Integrate with private DNS zone (Azure auto-creates
privatelink.blob.core.windows.net).
- Name:
Step 4: Test Connectivity
- Spin Up a Test VM:
- Deploy a small VM in
VNet-SecureHub(same subnet as your resources).
- Deploy a small VM in
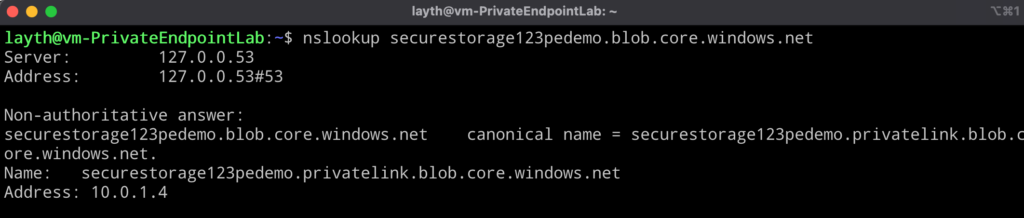
- Check DNS Resolution:
- SSH/RDP into the VM and run:bashCopynslookup securestorage123.blob.core.windows.net
nslookup securestorage123pedemo.blob.core.windows.net- ✅ Should return a private IP (e.g.,
10.0.1.4).
- Verify Access:
- Use Azure Storage Explorer or
curlwith a SAS token. If public access is blocked but private works you nailed it!
- Use Azure Storage Explorer or
Final Thoughts
Azure Private Endpoints let you balance accessibility and security like a pro. By keeping traffic off the public internet, you’re not just securing data you’re simplifying compliance and supercharging performance.
Ready to lock things down? Your cloud setup will thank you.