-

Calculated Chaos: The Strategic Value of M ..
1. Introduction Cybersecurity for cloud environments has traditionally relied on static defenses firewalls, ..
April 12, 2025 -

Denial-of-Wallet Attacks: How Unauthorized ..
Introduction Storage services like Microsoft Azure Storage Accounts and Amazon S3 buckets offer scalability, ..
April 6, 2025 -

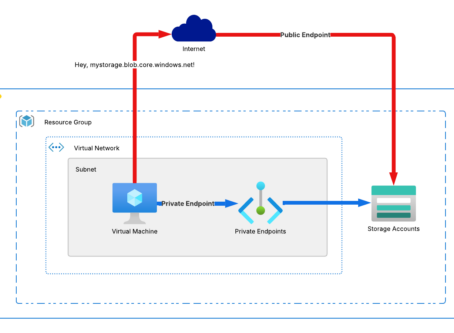
Your Data, Your Rules: Enforcing Privacy w ..
Introduction When your data travels over the public internet, it’s exposed to risks—interception, ..
February 21, 2025 -

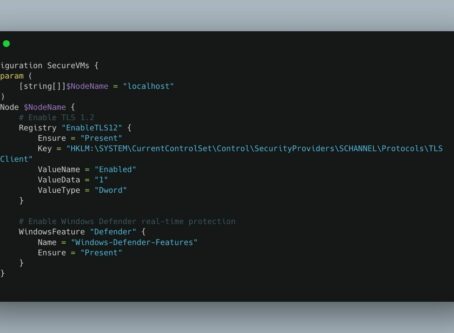
Automating Azure Security: Why DSC Is Your ..
Introduction Many organizations today overlook the critical role of Desired State Configuration (DSC) ..
February 16, 2025 -

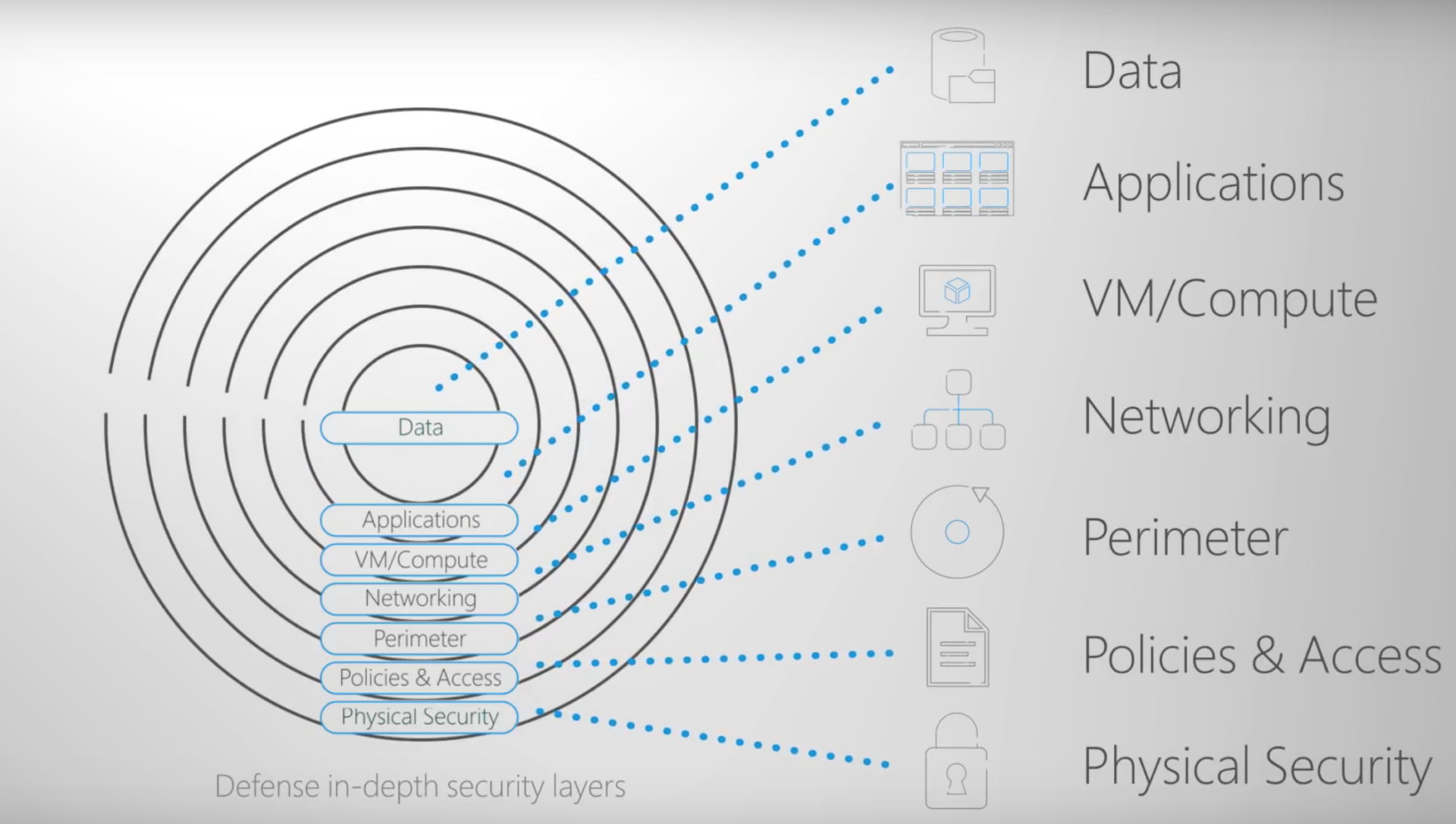
Defense in Depth in Azure: What You Should ..
As cloud adoption grows, so does the complexity of securing environments in platforms like Microsoft ..
October 14, 2024 -

Secure VM Access using Azure Bastion
Introduction In the cloud, security is a top priority. While Azure Virtual Machines (VMs) offer scalable ..
August 25, 2024 -

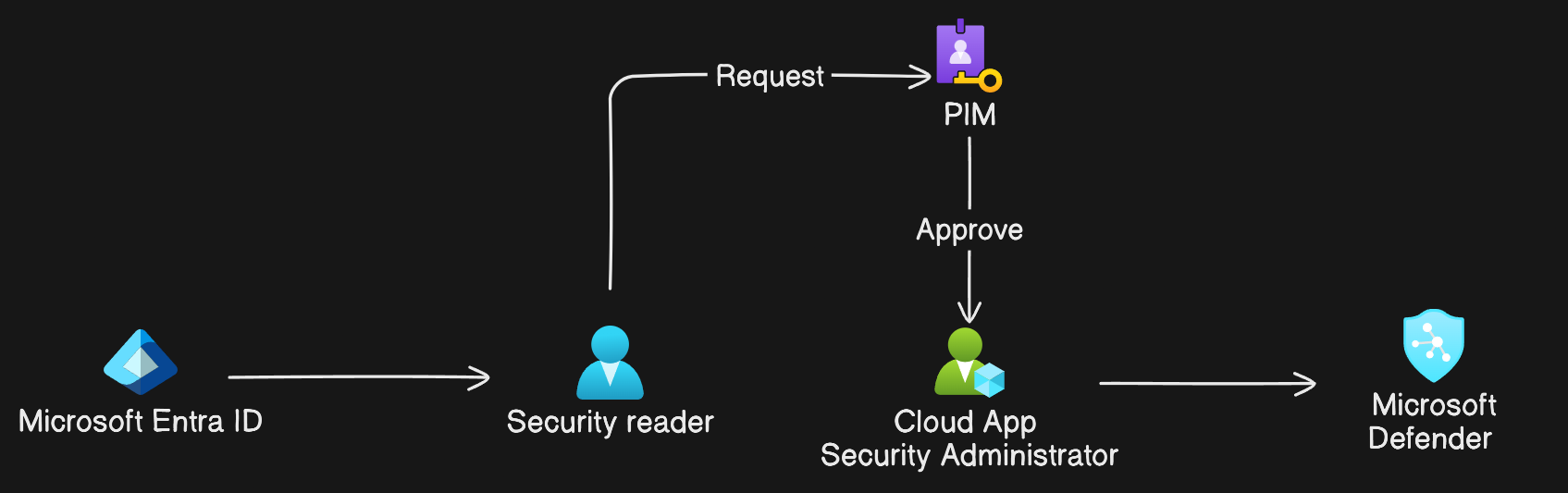
Understanding Microsoft Entra Privileged I ..
Introduction Microsoft Entra Privileged Identity Management (PIM) is a feature of Microsoft Entra ID that ..
August 4, 2024 -

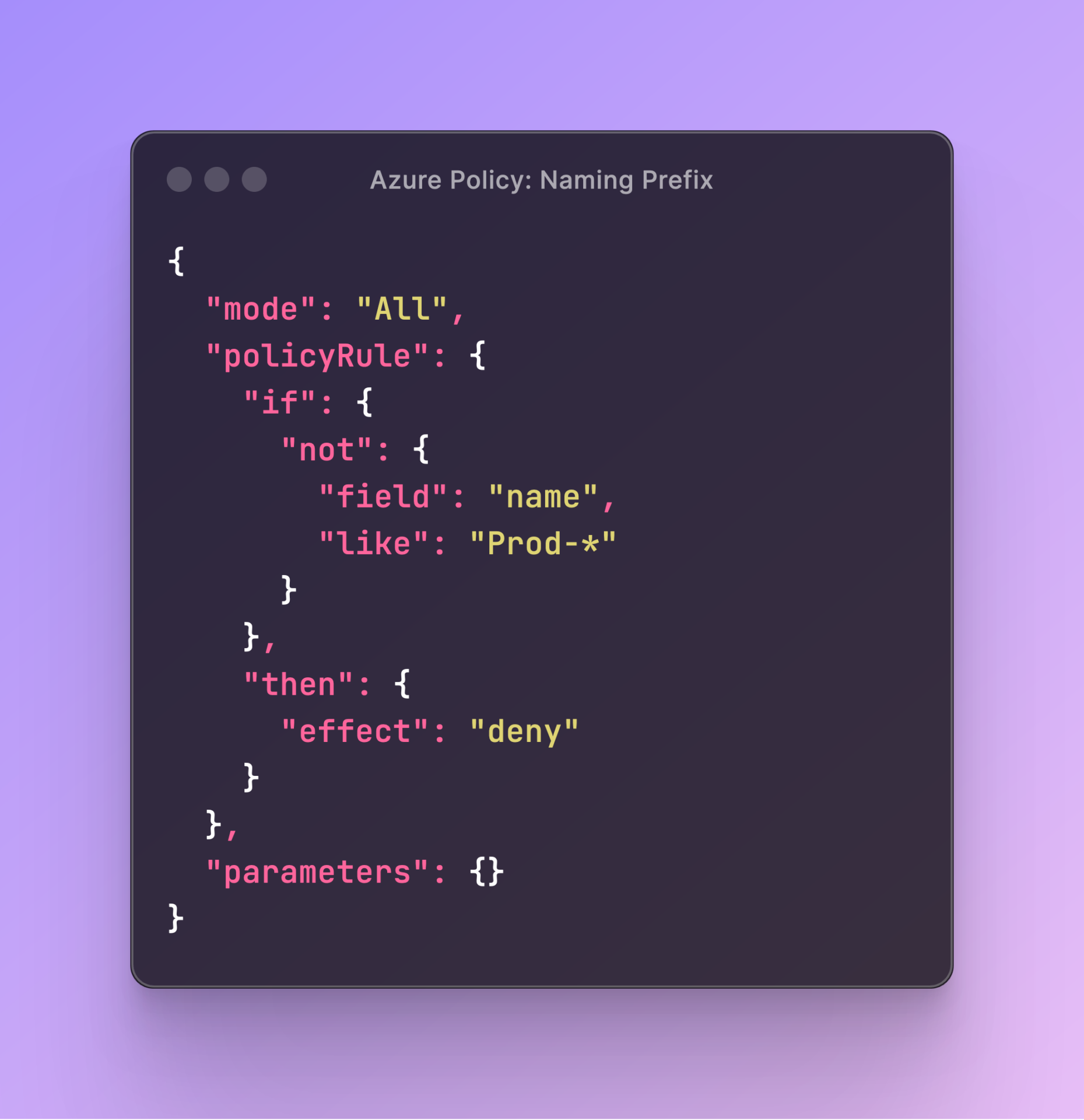
Azure Policy Anatomy Part 2: Building Cust ..
Introduction Now that we understand what Azure Policy is, and we’ve previously used a built-in ..
June 9, 2024 -

Is the Cloud Really Secure? Maybe yes mayb ..
Introduction When it comes to cloud security, one cannot help but ponder: Is the cloud truly secure? ..
April 7, 2024 -

Mastering Microsoft Defender for Cloud
Introduction In this blog series, we will delve into Microsoft Defender for Cloud. We’ll cover ..
March 24, 2024
End of content
No more posts to load