
-

Azure Service Groups: Finally, Resource Organization That Makes Business Sense
1Service Groups Architecture Overview Service Groups Deep Dive Infrastructure Perspective Definition and PurposeAzure Service Groups ..
September 7, 2025
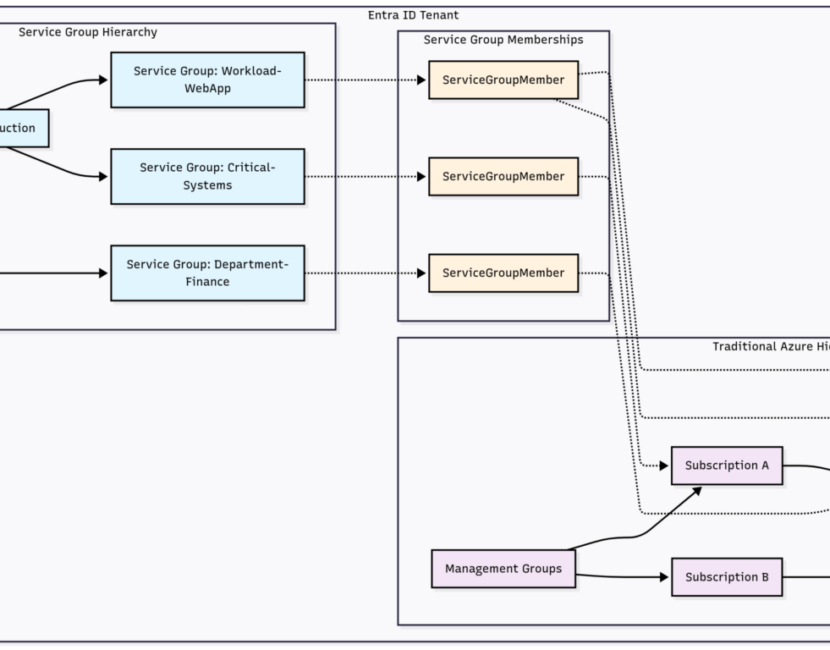
Service Groups Architecture Overview Service Groups Deep Dive Infrastructure Perspective Definition and PurposeAzure Service Groups ..