-
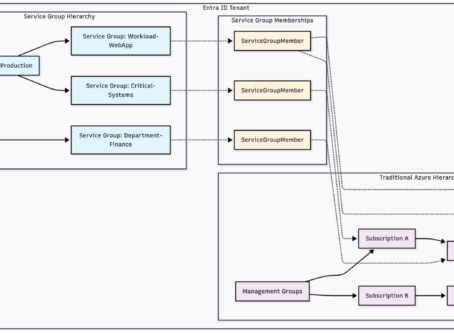
Azure Service Groups: Finally, Resource Or ..
Service Groups Architecture Overview Service Groups Deep Dive Infrastructure Perspective Definition and PurposeAzure ..
September 7, 2025 -

Calculated Chaos: The Strategic Value of M ..
1. Introduction Cybersecurity for cloud environments has traditionally relied on static defenses firewalls, ..
April 12, 2025 -

Denial-of-Wallet Attacks: How Unauthorized ..
Introduction Storage services like Microsoft Azure Storage Accounts and Amazon S3 buckets offer scalability, ..
April 6, 2025 -

Your Data, Your Rules: Enforcing Privacy w ..
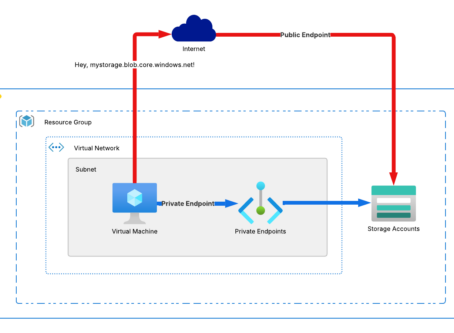
Introduction When your data travels over the public internet, it’s exposed to risks—interception, ..
February 21, 2025 -

Automating Azure Security: Why DSC Is Your ..
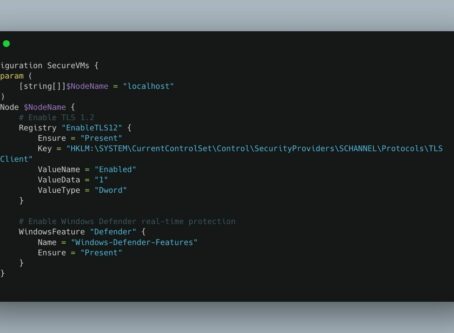
Introduction Many organizations today overlook the critical role of Desired State Configuration (DSC) ..
February 16, 2025 -

Secure, Compliant, and User-Friendly: The ..
Introduction With data breaches making headlines almost every day, organizations are increasingly prioritizing ..
November 2, 2024 -

Defense in Depth in Azure: What You Should ..
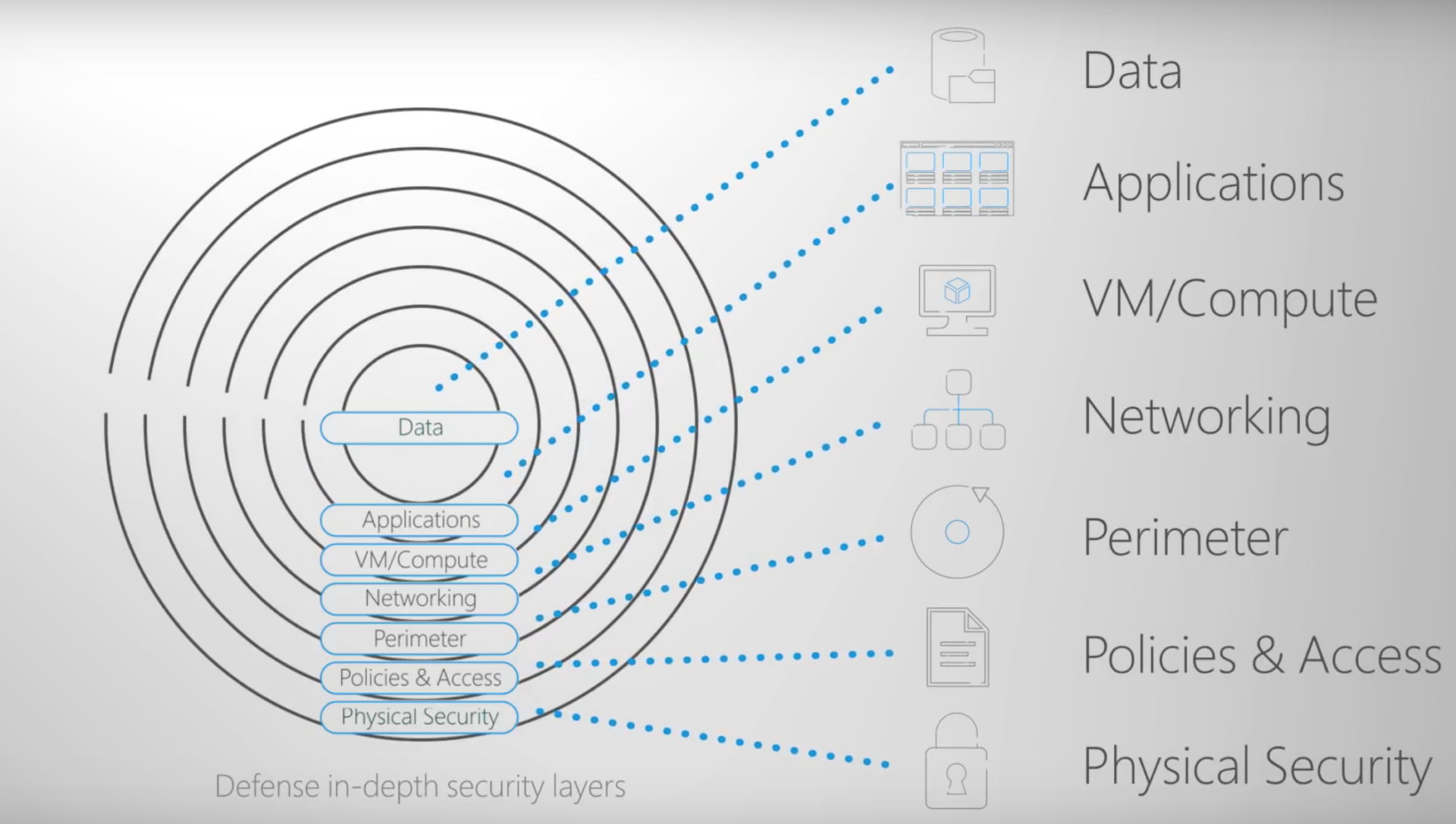
As cloud adoption grows, so does the complexity of securing environments in platforms like Microsoft ..
October 14, 2024 -

5 Quick Wins to Strengthen the Security of ..
Introduction In this article, i present a collection of actionable tips that require minimal effort but can significantly ..
September 15, 2024 -

Privilege escalation using Azure Service p ..
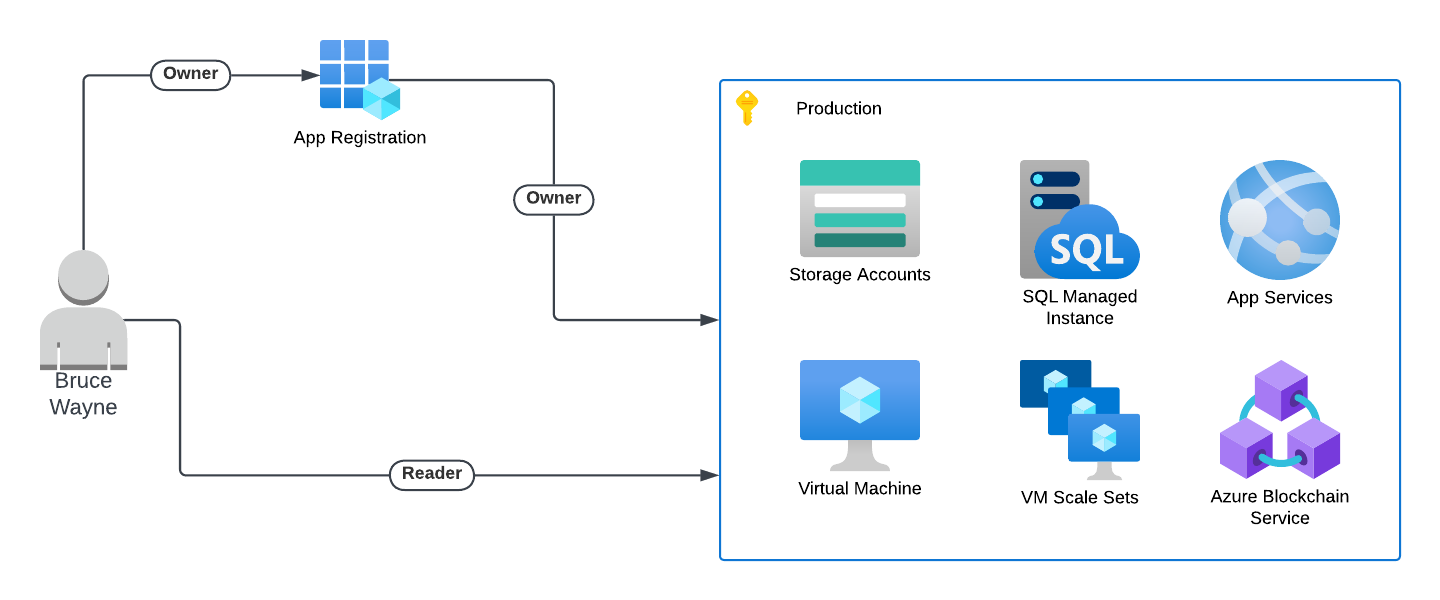
Introduction In Microsoft Azure, the management of access and permissions is critical for maintaining ..
September 1, 2024 -

Secure VM Access using Azure Bastion
Introduction In the cloud, security is a top priority. While Azure Virtual Machines (VMs) offer scalable ..
August 25, 2024
End of content
No more posts to load