Introduction
In this article, i present a collection of actionable tips that require minimal effort but can significantly strengthen your security posture. By implementing these quick wins, you can protect your Azure Virtual Machines (VMs) from potential threats and establish a more robust cloud infrastructure.
Avoid Associating Virtual Machines with Public IP Addresses
One of the simplest and most effective ways to improve security is by avoiding public IP addresses for your virtual machines. By default, Azure allows VMs to be assigned public IPs, which makes them accessible over the internet and susceptible to attacks. Instead, opt for private IP addresses and secure connections via VPNs or Azure Bastion. This not only reduces exposure to external threats but also creates a more controlled and secure environment.
Example:
❌ Bad Practice: Associating VMs with public IPs, leaving them exposed to direct internet traffic.
✔️ Best Practice: Using private IPs in conjunction with Azure Bastion for secure remote access.
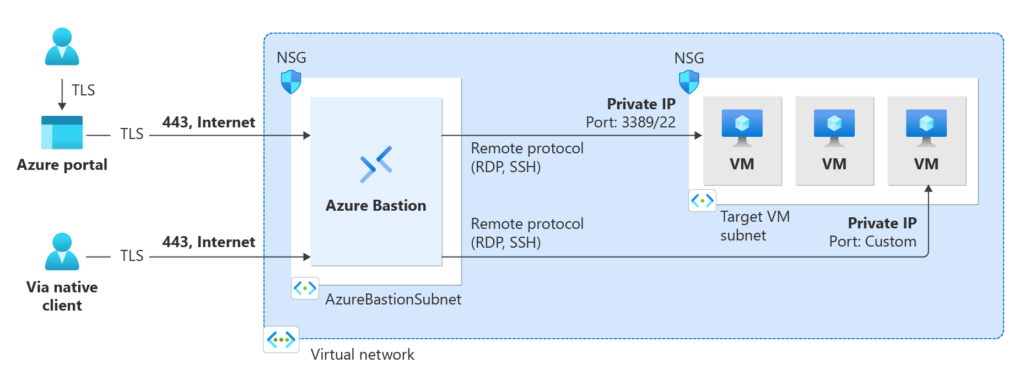
For more information on Azure Bastion, visit:
Use Network Security Groups (NSGs) to Control Network Traffic
Network Security Groups (NSGs) are a critical component in managing traffic to and from your Azure VMs. NSGs allow you to create filtering rules based on IP addresses, ports, and protocols, offering control over both inbound and outbound traffic. By configuring NSGs, you can:
- Limit inbound traffic to essential ports and specific IP ranges.
- Control outbound traffic to mitigate data exfiltration risks.
- Regularly review and update NSG rules to adapt to evolving security requirements.
Effective use of NSGs can reduce your VM’s attack surface, making your infrastructure more secure.
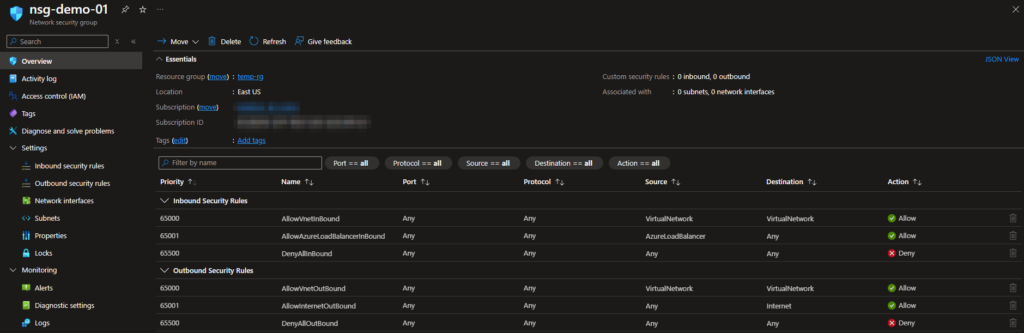
For more details, check out:
Enable Trusted Launch for Enhanced VM Security
Trusted Launch offers advanced protection against sophisticated threats like bootkits and rootkits. When enabled, it ensures that your VM boots only with trusted software, including verified boot loaders and operating systems. Key features of Trusted Launch include:
- Protection of cryptographic keys and certificates within the VM.
- Verification of the entire boot chain’s integrity.
- Additional security measures such as Secure Boot and virtual Trusted Platform Module (vTPM).
By enabling Trusted Launch during VM deployment, you take a proactive step in securing your virtual environment against emerging threats.
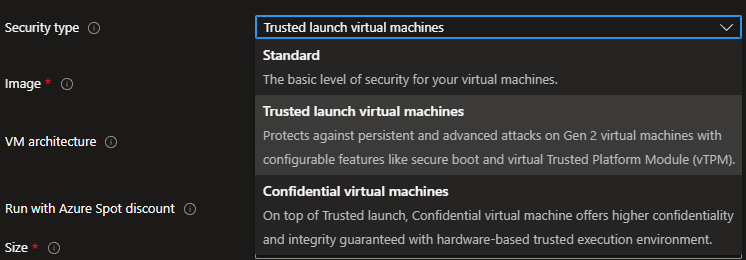
Learn more about Trusted Launch:
Integrate Microsoft Entra ID for VM Authentication
Using Microsoft Entra ID (formerly Azure AD) to authenticate VM access simplifies identity management and boosts security. By integrating Entra ID, you can:
- Eliminate the need for local administrator accounts, reducing the risk of credential theft.
- Enforce Multi-Factor Authentication (MFA) for an added layer of protection.
- Leverage Role-Based Access Control (RBAC) to manage who can access your VMs.
This centralized authentication method not only enhances security but also streamlines user and access management.
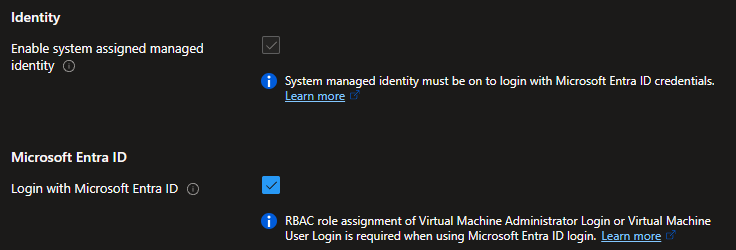
To learn more about Entra ID integration, visit:
Entra ID Authentication for VMs
Use Just-In-Time (JIT) VM Access
Just-In-Time (JIT) access is a powerful feature that reduces exposure to attacks by limiting the window during which VMs are accessible. With JIT, you can:
- Control which ports are open and for how long.
- Automatically lock down inbound traffic by default, opening ports only when necessary.
- Grant temporary access based on user requests that are routed through Azure RBAC.
This approach reduces the risk of unauthorized access while ensuring legitimate users can connect to VMs only when needed.
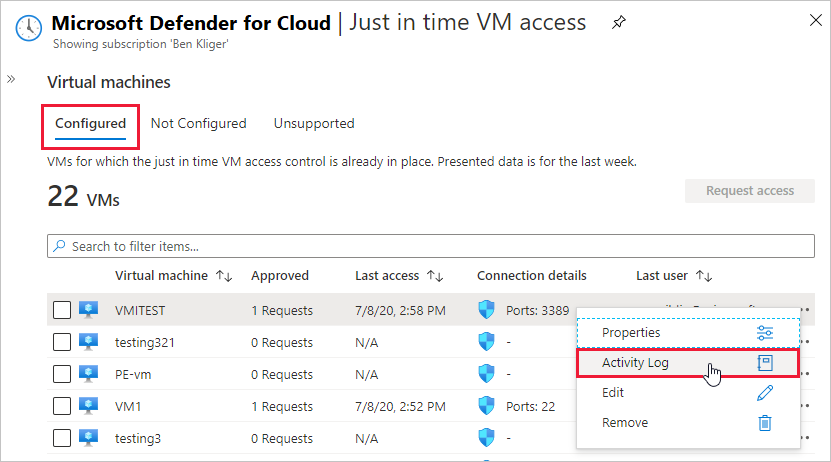
For more information, visit:

