Introduction
In Microsoft Azure, the management of access and permissions is critical for maintaining a secure environment. Azure Service Principals serve as non-human identities that allow applications to authenticate and interact with Azure resources. However, if a Service Principal is misconfigured or compromised, it can lead to privilege escalation, granting unauthorized access to critical resources. This article provides an in-depth examination of Azure Service Principals, their potential misuse, and the mitigation techniques to secure them effectively.
What is an Application Registration?
An Application Registration in Azure is the process of registering an application with Azure Active Directory (Azure AD). This registration establishes a trust relationship between the application and the Microsoft identity platform, enabling the application to authenticate users and access resources securely. When an application is registered, it receives a unique application (client) ID and can be configured with permissions to access various Azure resources. This setup is essential for implementing role-based access control (RBAC), ensuring that applications have only the permissions they need to function effectively while minimizing security risks.
What is a service principal?
A Service Principal is an identity created in Entra ID specifically for applications or services. It acts as a security identity that applications use to authenticate against Azure resources. Unlike user accounts, which are tied to individual users, service principals are designed for automated tools, scripts, and applications, allowing them to access Azure resources without direct user intervention. Service principals can be granted permissions similar to user accounts, enabling them to perform actions on Azure resources. This includes roles such as Owner or Contributor, which can be assigned to control access levels.
How Can Service Principal Abuse Occur?
Service principal abuse can occur through several vectors:
- Credential Theft: Attackers may exploit vulnerabilities in applications or use phishing techniques to steal credentials associated with a service principal.
- Misconfiguration: Incorrectly configured service principals can inadvertently grant excessive access to resources. For example, if a service principal is assigned to a role that has permissions to delete resources, it could lead to data loss.
- Insecure Development Practices: Poor coding practices, such as hardcoding credentials in application code, can expose service principal credentials to attackers.
- Lack of Governance: Without proper governance and oversight, organizations may fail to regularly review and revoke unnecessary service principals or permissions, creating potential entry points for attackers.
- Unmonitored Activity: Lack of monitoring can allow malicious activities to go unnoticed. If service principal activities are not logged or audited, it becomes difficult to detect abuse until significant damage has been done.
Scenario: Privilege Escalation via Service Principal Misconfiguration
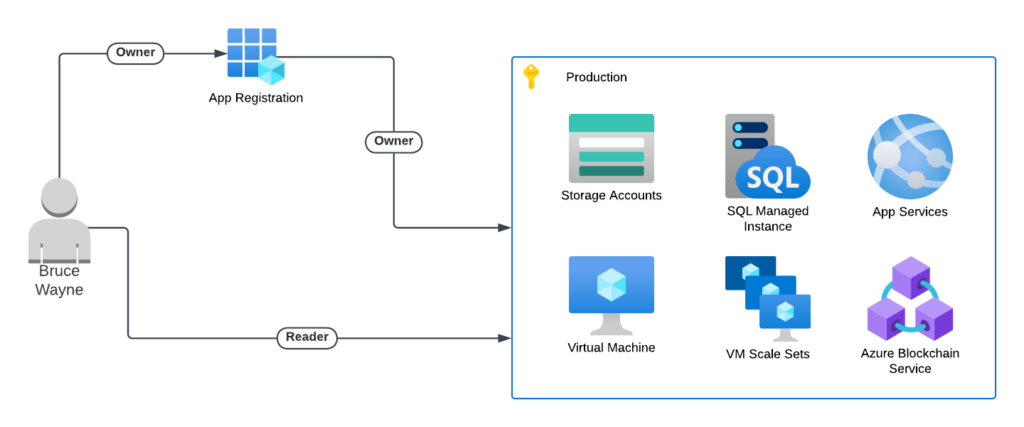
Initial Setup:
- User Role: A user named Bruce Wayne has been assigned the Reader role at the subscription level, which allows him to view resources but not modify them.
- Application Registration: Bruce is also the owner of an application registered in Entra ID, which has been assigned the Owner role at the subscription level through its associated Service Principal. This role allows the application to create and manage resources within the subscription.
Privilege Escalation Process:
- Access to Application: Since Bruce is the owner of the application, he has full control over the application settings and its associated Service Principal. This includes the ability to modify permissions and roles assigned to the Service Principal.
- Role Assignment Manipulation: Bruce can use her ownership privileges to modify his permissions. He can use the application to execute commands that allow him to assign himself a higher role within the subscription, such as Owner or Contributor, despite his original Reader role. For example, he might use Azure CLI commands to elevate his privileges:
az role assignment create --assignee "[email protected]" --role "Owner" --scope "/subscriptions/Production"- Escalated Access: After executing the above command, Bruce now has Owner access, effectively granting him elevated permissions that allow him to create, modify, or delete resources in the subscription. This action circumvents the restrictions imposed by his original Reader role.
- Exploitation of Elevated Privileges: With Owner access, Bruce can now perform actions such as:
- Creating new resources (e.g., virtual machines, storage accounts).
- Deleting existing resources.
- Assigning roles and permissions to other users or Service Principals, potentially creating further pathways for escalation or unauthorized access.
How do we protect against service principle abuse?
To mitigate the risks associated with service principal abuse, organizations should adopt the following best practices:
- Principle of Least Privilege: Always assign the minimum permissions necessary for a service principal to function. Regularly review and adjust permissions as needed.
- Strong Authentication Methods: Use strong authentication methods, such as certificates instead of client secrets, and ensure that secrets are rotated regularly.
- Monitoring and Auditing: Implement logging and monitoring to track activities associated with service principals. Regular audits can help identify unusual patterns or unauthorized access attempts.
- Regular Reviews: Periodically review all service principals and their associated permissions. Remove any that are no longer needed and ensure that permissions are appropriate for their intended use.
- Security Training: Educate developers and administrators about secure coding practices and the importance of safeguarding service principal credentials.
Conclusion
Azure Service Principals are essential for managing access to Azure resources securely. However, if not managed properly, they can become a significant security risk and a vector for privilege escalation. By understanding the nature of service principals, recognizing how they can be abused, and implementing security measures, organizations can protect their Azure environments from potential threats. Following best practices for managing service principals is necessary for maintaining a secure cloud infrastructure.