Introduction
In the cloud, security is a top priority. While Azure Virtual Machines (VMs) offer scalable and flexible computing power, improper configuration—especially when exposing VMs directly to the internet—can introduce serious security vulnerabilities. This article delves into the risks associated with public IP exposure for Azure VMs and demonstrates how Azure Bastion serves as a powerful solution to effectively safeguard these critical resources.
Risks of Exposing Azure Virtual Machines Directly to the Internet
- Increased Attack Surface:
- When Azure VMs are exposed directly to the internet, they become accessible to anyone, including malicious actors. Hackers can easily discover public IP addresses through automated scans and attempt to exploit vulnerabilities via brute-force attacks or other methods.
- Brute-Force Attacks:
- RDP (Remote Desktop Protocol) and SSH (Secure Shell) ports are common targets for brute-force attacks. By guessing usernames and passwords, attackers can gain unauthorized access to your VMs, leading to data breaches, ransomware, and other severe consequences.
- Exploitation of Unpatched Vulnerabilities:
- Exposed VMs are at higher risk of exploitation if they are not regularly patched. Cybercriminals often exploit known vulnerabilities in operating systems or applications to compromise a VM, which can result in data loss or service disruption.
- Data Exfiltration and Loss:
- Once a VM is compromised, sensitive data can be exfiltrated. This not only damages your reputation but can also lead to compliance violations, financial losses, and legal repercussions.
- Resource Hijacking:
- Attackers can hijack your VM resources for illegal activities like cryptojacking, where they use your compute power to mine cryptocurrency, leading to unexpected costs.
How to Protect Azure Virtual Machines Using Azure Bastion
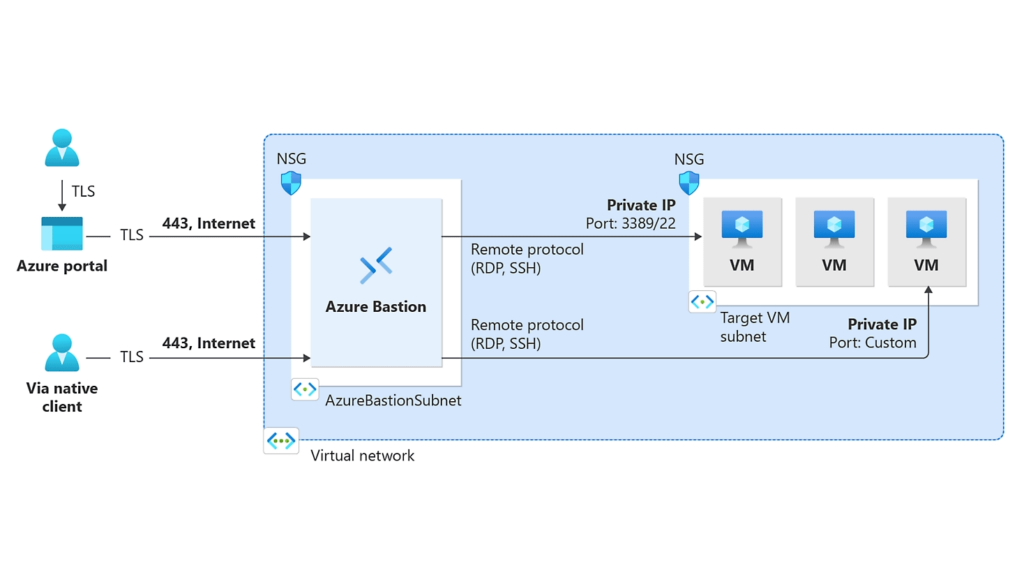
Introduction to Azure Bastion
Azure Bastion is a fully managed platform-as-a-service (PaaS) solution that provides secure and seamless RDP and SSH connectivity to Azure VMs directly through the Azure portal, without exposing VMs to the public internet.
Key Features of Azure Bastion:
- No Public IPs Needed: Azure Bastion allows you to access your VMs without requiring a public IP, reducing the attack surface significantly.
- Seamless and Secure Connectivity: Azure Bastion provides SSL-encrypted RDP/SSH connections directly from the Azure portal, eliminating the need for a VPN or a client.
- Protection Against Network Attacks: By removing the need for public IPs, Azure Bastion helps protect against network attacks such as brute-force attacks on RDP/SSH ports.
- Native Integration: Azure Bastion integrates natively with your virtual network, offering a streamlined experience without additional configuration.
| SKU | Features |
|---|---|
| Developer | – Connect to target VMs in the same virtual network – Connect to Linux VM using SSH – Connect to Windows VM using RDP – VM audio output |
| Basic | – Connect to target VMs in the same virtual network – Connect to target VMs in peered virtual networks – Support for concurrent connections – Access Linux VM Private Keys in Azure Key Vault (AKV) – Connect to Linux VM using SSH – Connect to Windows VM using RDP – Kerberos authentication – VM audio output |
| Standard | – Connect to target VMs in the same virtual network – Connect to target VMs in peered virtual networks – Support for concurrent connections – Access Linux VM Private Keys in Azure Key Vault (AKV) – Connect to Linux VM using SSH – Connect to Windows VM using RDP – Connect to Linux VM using RDP – Connect to Windows VM using SSH – Specify custom inbound port – Connect to VMs using Azure CLI – Host scaling – Upload or download files – Kerberos authentication – Shareable link – Connect to VMs via IP address – VM audio output – Disable copy/paste (web-based clients) |
| Premium | – Connect to target VMs in the same virtual network – Connect to target VMs in peered virtual networks – Support for concurrent connections – Access Linux VM Private Keys in Azure Key Vault (AKV) – Connect to Linux VM using SSH – Connect to Windows VM using RDP – Connect to Linux VM using RDP – Connect to Windows VM using SSH – Specify custom inbound port – Connect to VMs using Azure CLI – Host scaling – Upload or download files – Kerberos authentication – Shareable link – Connect to VMs via IP address – VM audio output – Disable copy/paste (web-based clients) – Session recording – Private-only deployment |
Implementing Azure Bastion
Deployment: Azure Bastion can be easily deployed in your virtual network. Once deployed, you can connect to any VM in that VNet using the “Connect” button in the Azure portal.
No Changes to VM Required: You don’t need to install or configure any software on your VMs. Azure Bastion works out of the box, leveraging the existing RDP/SSH client on the Azure portal.
Scaling and Availability: Azure Bastion is highly available, and scales automatically to accommodate the number of concurrent connections, ensuring reliable access to your VMs.
In this guide, we will walk through the process of deploying Azure Bastion in the West US region and using it to securely access a Windows Server VM. Deploying Azure Bastion is a straightforward process that enhances the security of your virtual machines by eliminating the need for public IP addresses.
For detailed instructions, you can refer to the official documentation https://learn.microsoft.com/en-us/azure/bastion/quickstart-host-portal
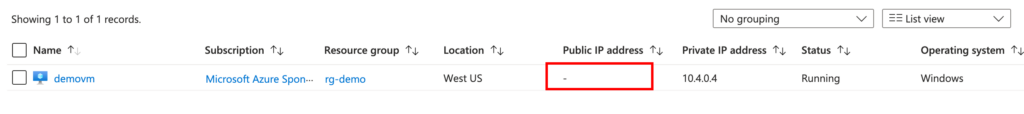
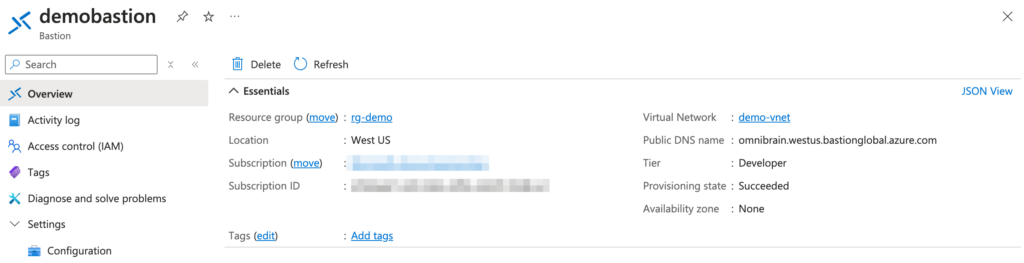
Once the Bastion deployment is complete, follow these steps to connect to your Windows Server VM securely:
- Open the Connect Pane: After the deployment finishes, the screen will change to the Connect pane.
- Enter Authentication Credentials: Input your username and password for the Windows Server VM.
- Establish the Connection: Click on Connect. The connection will open directly in the Azure portal using HTML5 over port 443.
- Clipboard Permissions: When prompted for clipboard permissions, select Allow. This will enable clipboard functionality between your local machine and the remote VM.
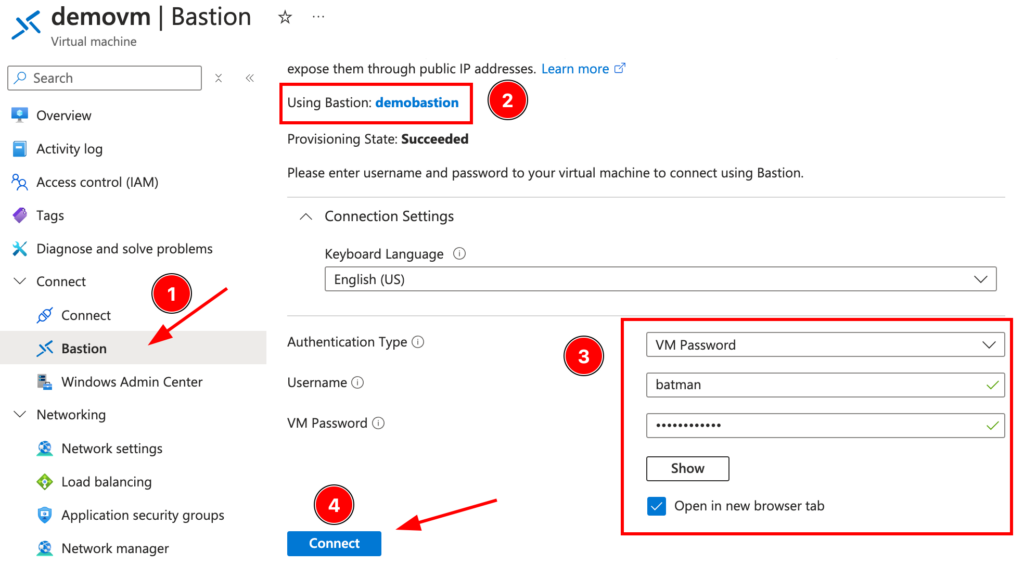
And that’s it! You now have a secure RDP session to your Windows Server VM without exposing it publicly or associating it with a public IP address.
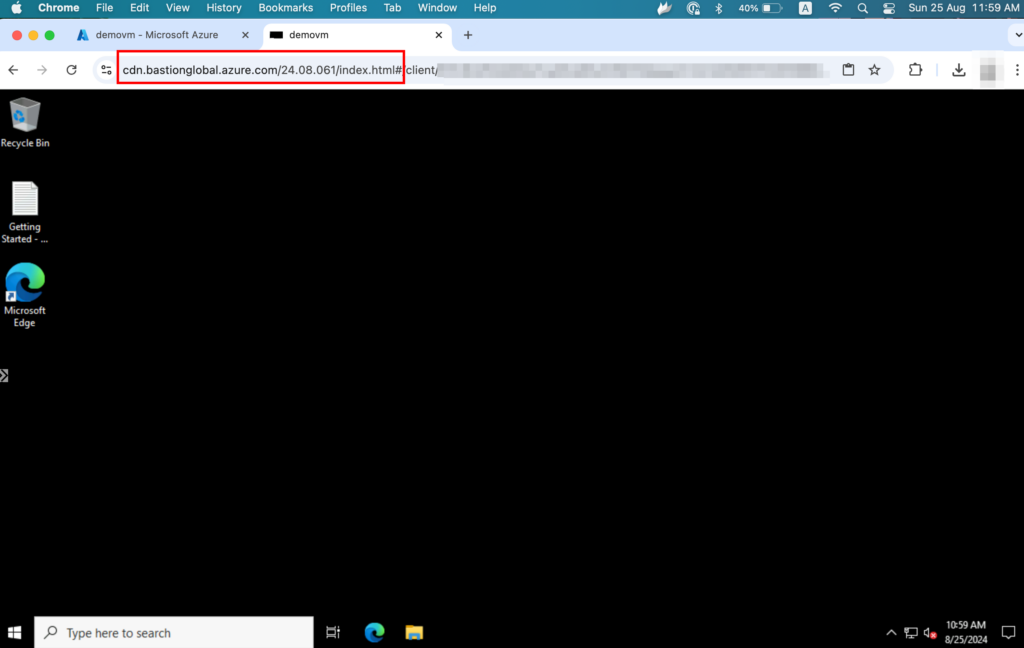
Best Practices for Secure VM Access:
Use Azure Bastion with Just-in-Time (JIT) Access: Combine Azure Bastion with JIT VM access to limit the time frame in which the VMs can be accessed.
Implement Network Security Groups (NSGs): Use NSGs to further restrict access to your VMs and control inbound and outbound traffic within your virtual network.
Conclusion
Exposing Azure Virtual Machines directly to the internet introduces significant security risks, leaving them vulnerable to a wide range of cyber threats. Azure Bastion offers a robust solution by eliminating the need for public IPs, thereby minimizing the attack surface while ensuring secure, seamless access to your VMs. Incorporating Azure Bastion into your security strategy not only fortifies your cloud environment but also provides a critical layer of protection against unauthorized access and malicious activities.

