Introduction
To fully grasp the concept of agentless scanning in Microsoft Defender for Cloud, it’s essential to delve into a few key questions that will shed light on this innovative feature. Firstly, what exactly is agentless scanning? Understanding this will provide the foundation for our discussion. Next, we’ll explore how agentless scanning operates, unraveling the mechanisms behind its functionality and why it offers a distinct advantage. Finally, we will guide you through the steps required to enable agentless scanning, ensuring you can leverage this tool effectively. Through this comprehensive exploration, you’ll gain a thorough understanding of agentless scanning and how it can enhance your cloud security strategy.
What is agentless scanning?
Agentless scanning refers to the process of evaluating and analyzing systems, networks, and devices without the need to install any software agents on the devices being scanned. This approach uses network-based techniques to gather information and assess the security posture or compliance status of the target systems.
Key characteristics and benefits of agentless scanning include:
- No Software Installation: There’s no need to deploy software agents on the target devices, which simplifies deployment and reduces administrative overhead.
- Minimal System Impact: Because there are no agents running on the devices, there’s little to no performance impact on the systems being scanned.
- Broad Coverage: It can scan a wide range of devices, including those that may not support agent-based solutions, such as IoT devices, printers, and network equipment.
- Ease of Maintenance: Without agents to manage, there’s no need for updates or troubleshooting of agent software on multiple devices.
- Quick Deployment: Agentless scanning can be quickly implemented and configured, providing immediate insights without the delay of deploying agents.
How does agentless scanning work?
Agentless scanning in Microsoft Defender for Cloud collects data from virtual machines (VMs) using cloud APIs. It takes snapshots of VM disks, performing an out-of-band analysis of the operating system configuration and file system without affecting the VM. The metadata extracted from these snapshots is analyzed to detect configuration gaps and potential threats. Snapshots are deleted after metadata collection, ensuring minimal data retention. This process supports broad visibility, vulnerability assessment, secret scanning, and threat detection without installing agents or impacting performance.
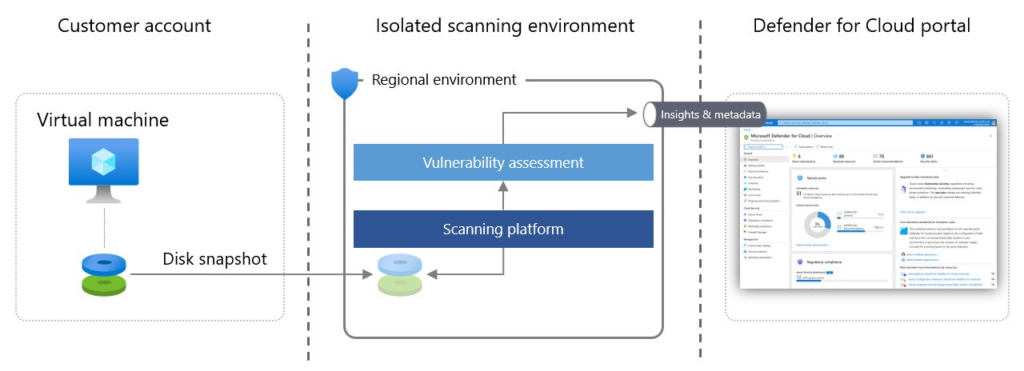
Why use agentless scanning?
Choosing between agentless and agent-based scanning in Microsoft Defender for Cloud largely depends on your specific use case and environment. Each approach has unique features and benefits that can align differently with your security needs. To aid in making an informed decision, I have compiled a comparison of key features and advantages of both agentless and agent-based scanning. This comparison will help you understand which option may be best suited for your cloud security strategy.
| Feature | Agentless Scanning | Agent-Based Scanning |
|---|---|---|
| Data Collection Method | Cloud APIs and disk snapshots | Agents installed on VMs |
| Performance Impact | Minimal, no impact on VM performance | Potential impact due to agent running on VMs |
| Setup | No installation required | Requires agent installation and maintenance |
| Visibility | Broad, out-of-band analysis | Detailed, real-time monitoring |
| Data Retention | Snapshots deleted after metadata extraction | Continuous data collection |
| Vulnerability Assessment | Supported | Supported |
| Configuration Analysis | Supported | Supported |
| Threat Detection | Supported | Supported |
| Secret Scanning | Supported | Supported |
How to enable agentless scanning?
Prerequisites
Agentless scanning is automatically enabled when you onboard your VMs to either the Defender Cloud Security Posture Management (CSPM) plan or the Defender for Servers P2 plan. If you already have Defender for Servers P2 enabled and agentless scanning is turned off, you can easily enable it by following these steps:
- Open the Environment settings in Microsoft Defender for Cloud and select the relevant account or project.
- For either the CSPM or Defender for Servers P2 plan, navigate to Settings and turn on Agentless scanning for machines.
- Save the changes and proceed to configure access based on your cloud environment (Azure, AWS, or GCP).
Unlike agent-based scanning in Defender for Servers you can exclude servers from being scanned.
Demonstration
In this case, we are going to enable the agentless scanning from Microsoft Defender CSPM so this feature needs to be enabled
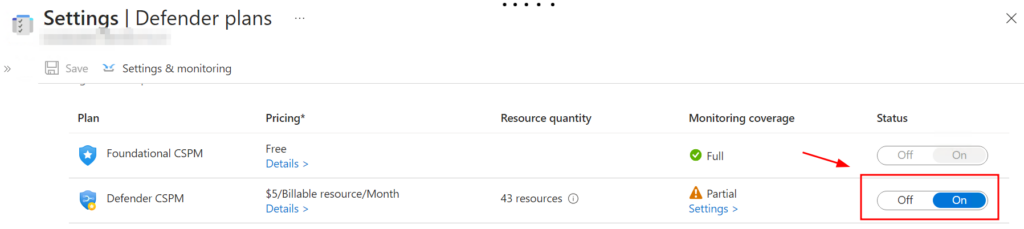
Next, click on the settings to configure Defender CSPM and we make sure the Agentless scanning for Machines is enabled.
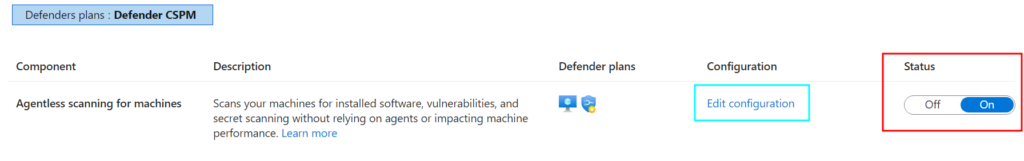
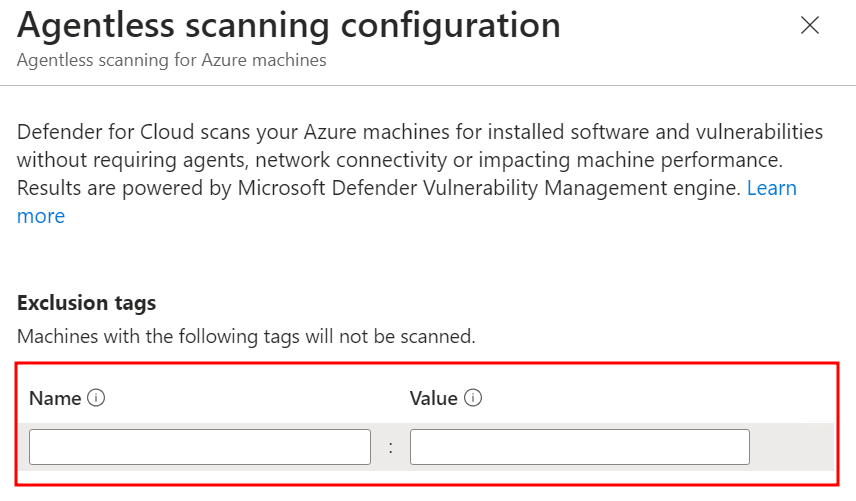
Agentless scanning will be enabled for all the virtual machines but if you want to exclude virtual machines you click on Edit Configurations and exclude the virtual machines you want using exclusion tags
And for this demo, I have installed a “Dibizor” Mallware on a virtual machine it was detected by the Agentless Scanning Engine as shown in the following screenshot
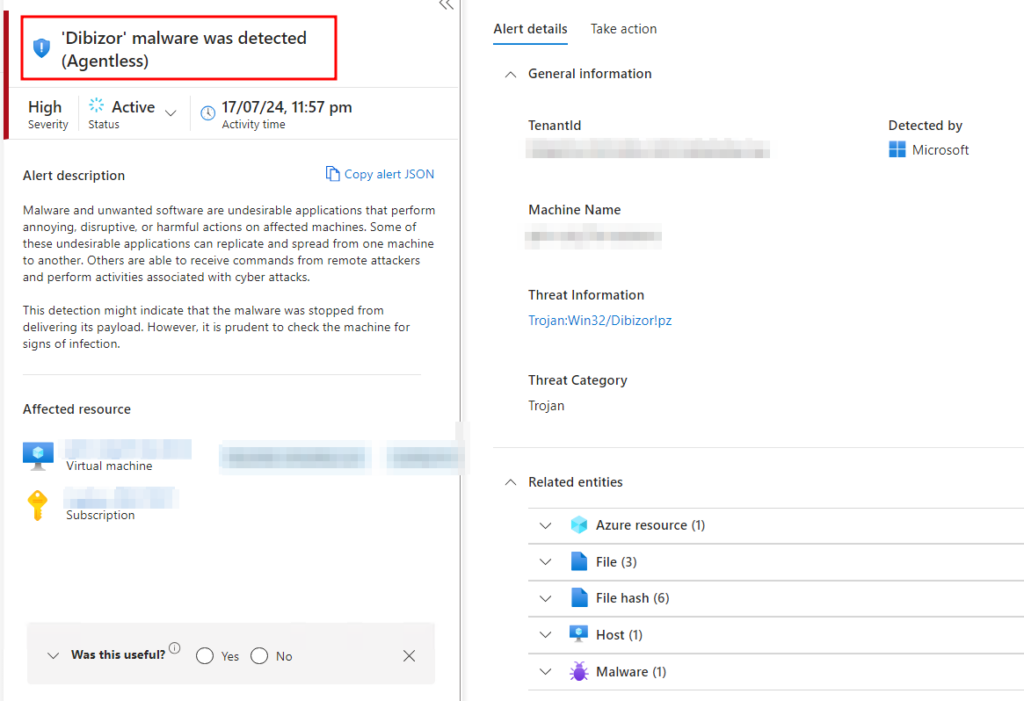
Conclusion
Agentless scanning in Microsoft Defender for Cloud is a powerful tool that enables organizations to assess the security of their cloud environments without the need for installed agents or network connectivity. By providing broad visibility, deep analysis, vulnerability assessment, secret scanning, and malware detection, agentless scanning helps identify and mitigate security risks, ensuring the overall health and resilience of your cloud infrastructure.

