-
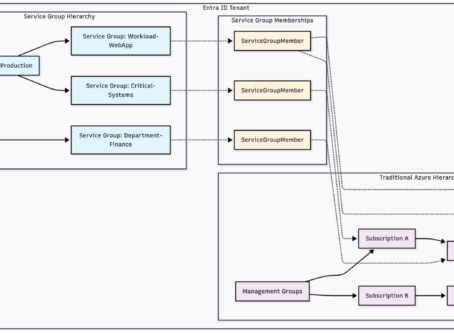
Azure Service Groups: Finally, Resource Or ..
Service Groups Architecture Overview Service Groups Deep Dive Infrastructure Perspective Definition and PurposeAzure ..
September 7, 2025 -

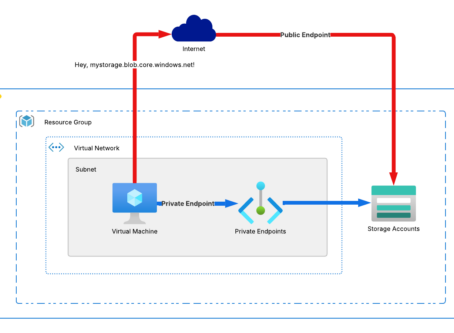
Your Data, Your Rules: Enforcing Privacy w ..
Introduction When your data travels over the public internet, it’s exposed to risks—interception, ..
February 21, 2025 -

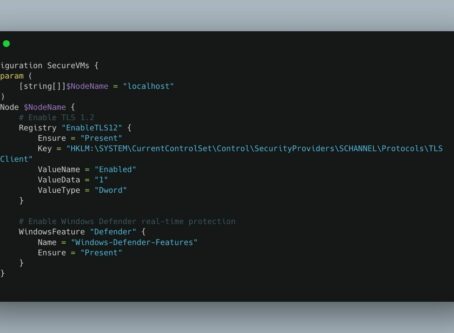
Automating Azure Security: Why DSC Is Your ..
Introduction Many organizations today overlook the critical role of Desired State Configuration (DSC) ..
February 16, 2025 -

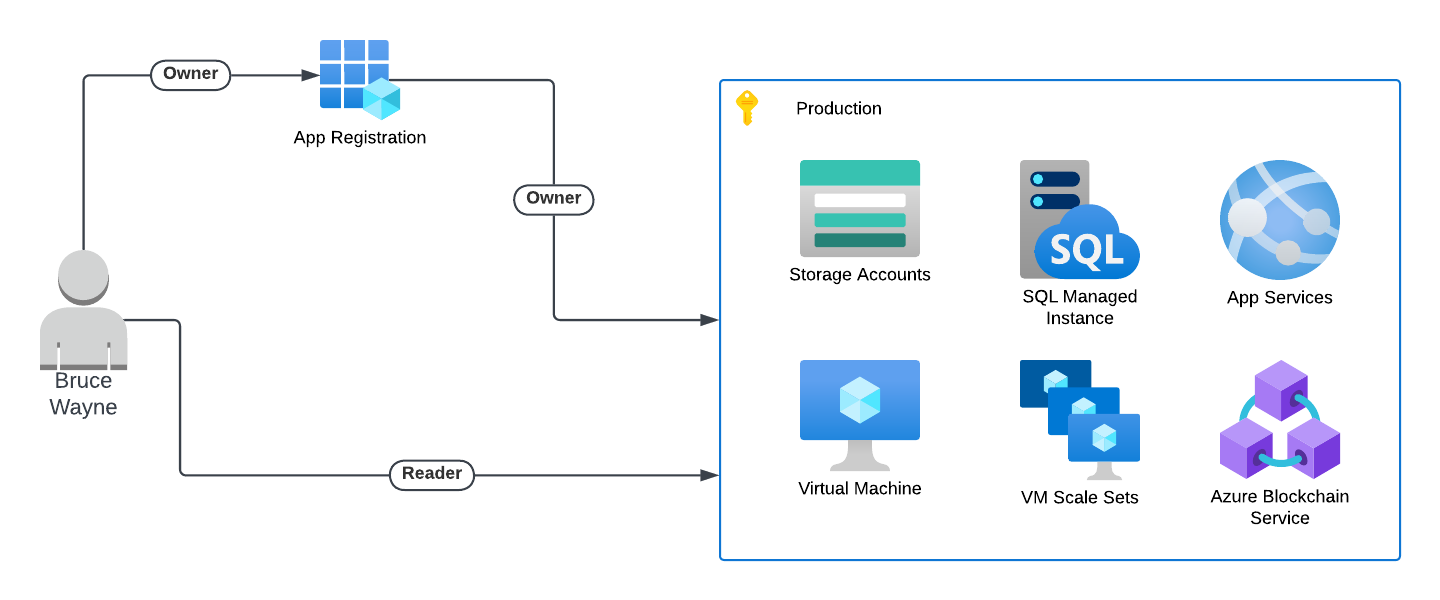
Privilege escalation using Azure Service p ..
Introduction In Microsoft Azure, the management of access and permissions is critical for maintaining ..
September 1, 2024 -

Secure VM Access using Azure Bastion
Introduction In the cloud, security is a top priority. While Azure Virtual Machines (VMs) offer scalable ..
August 25, 2024 -

Agentless scanning using Microsoft Defende ..
Introduction To fully grasp the concept of agentless scanning in Microsoft Defender for Cloud, it’s ..
July 28, 2024 -

Understanding MAC Address Changes in Azure ..
This Blog post will show you how to change mac address in azure vm permanently.
April 21, 2024 -

Azure Infiltrated: How Attackers Exploit M ..
Introduction Cloud computing has become increasingly popular among enterprises, corporations, and individuals, ..
February 4, 2024
End of content
No more posts to load