Introduction
Many organizations today overlook the critical role of Desired State Configuration (DSC) in safeguarding cloud infrastructure, often underestimating its ability to prevent misconfigurations, enforce compliance, and mitigate security risks. In Azure environments, this oversight can lead to vulnerabilities, as DSC serves as a cornerstone for automating secure configurations, ensuring policy adherence, and maintaining consistency across virtual machines (VMs). Yet, when leveraged effectively, DSC transforms into a proactive shield enabling organizations to codify security postures, remediate drift in real time, and align with regulatory standards. This article examines how Azure DSC strengthens security frameworks, outlines its strategic advantages, and provides actionable best practices for implementation to help businesses turn configuration management into a competitive asset.
What is Desired State Configuration (DSC)?
DSC is a PowerShell-based configuration management tool that allows administrators to define and enforce the desired state of a system. It offers:
- Compliance Policy Enforcement: Ensures systems adhere to security standards.
- Automatic Remediation: Detects and corrects configuration drifts automatically.
- Least Privilege Principle: Reduces the attack surface by enforcing strict security configurations.
DSC in Azure for Security
Azure provides two main approaches to using DSC for security:
- Azure Automation DSC
- A hosted DSC service within Azure Automation.
- Enables centralized management of security policies and compliance tracking.
- Facilitates the enforcement of critical settings such as encryption, firewall rules, and privileged access restrictions.
- Standalone DSC on Azure Virtual Machines
- DSC configurations can be applied directly to Azure VMs.
- Ideal for enforcing security policies in isolated environments.
Lab: Enforcing Security Policies on Azure VMs with Azure Automation DSC
Objective
In this lab, we will use Azure Automation DSC to enforce security baselines on Azure virtual machines. The configuration will:
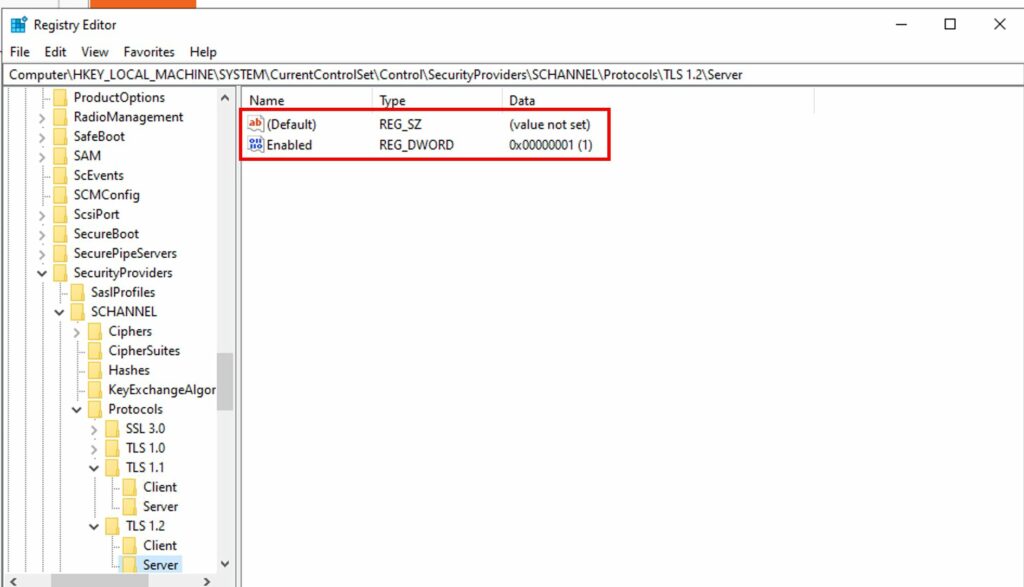
- Enable TLS 1.2 to enhance communication security.
- Ensure that Windows Defender real-time protection is enabled.
Prerequisites
- An active Azure subscription.
- An Azure Automation account with DSC enabled.
- At least one Azure Virtual Machine (Windows) to apply the DSC configuration.
Step 1: Create an Azure Automation Account
- Navigate to the Azure Portal → Automation Accounts.
- Click Create and provide the following details:
- Name: SecureAutomationDSC
- Resource Group: Select or create one.
- Region: Choose an appropriate region.
- Enable System Managed Identity: Yes
- Click Create.
Step 2: Create and Import the DSC Configuration
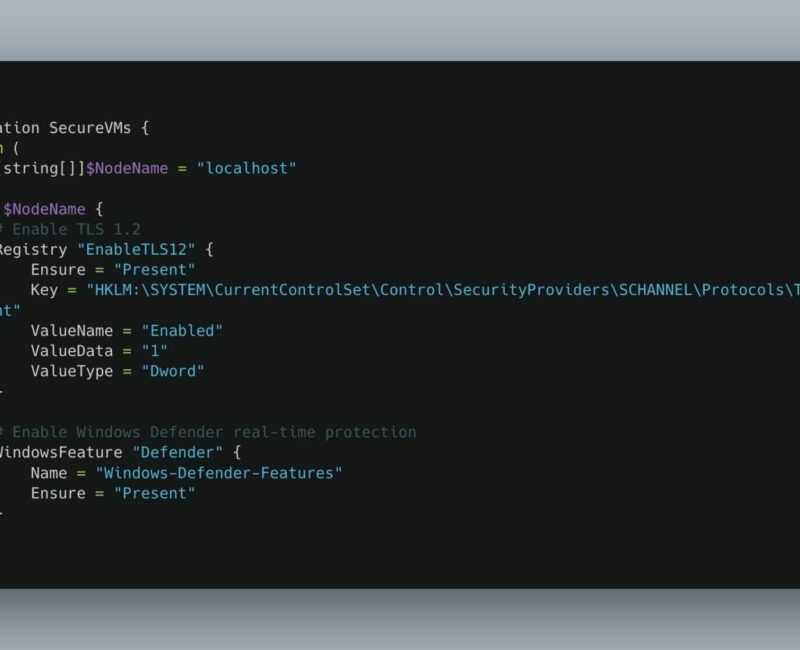
- Import the following PowerShell DSC script:
Configuration SecureVMs {
param (
[string[]]$NodeName = "localhost"
)
Node $NodeName {
# Enable TLS 1.2
Registry "EnableTLS12" {
Ensure = "Present"
Key = "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client"
ValueName = "Enabled"
ValueData = "1"
ValueType = "Dword"
}
# Enable Windows Defender real-time protection
WindowsFeature "Defender" {
Name = "Windows-Defender-Features"
Ensure = "Present"
}
}
}Import-AzAutomationDscConfigurtion -Published -AutomationAccountName "AutomationAccountName" -ResourceGroupName "ResourceGroupName" -SourcePath "SourcePathofthepowershellScript" -Force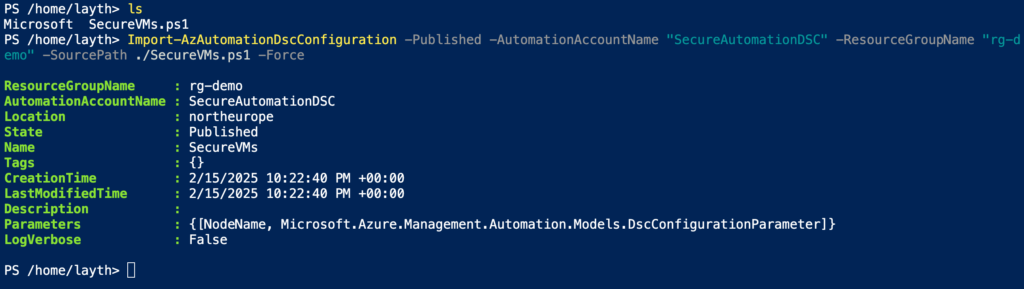
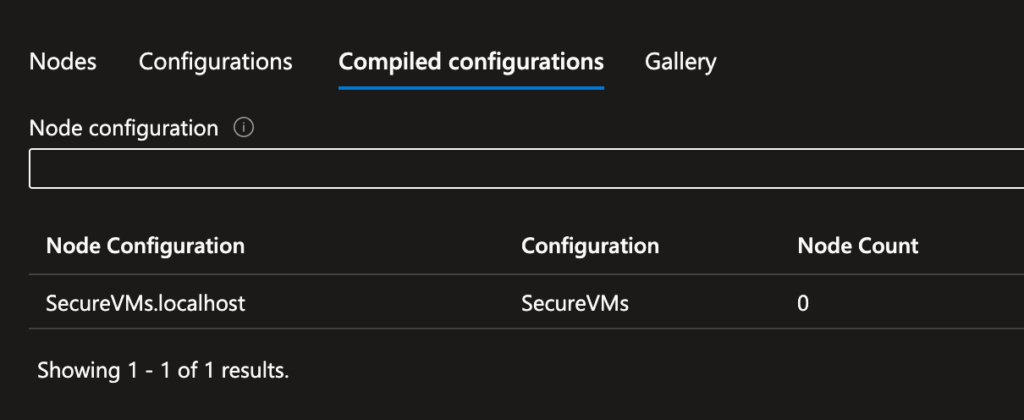
Step 3: Compile and Assign the DSC Configuration
- Select the uploaded configuration and click Compile.
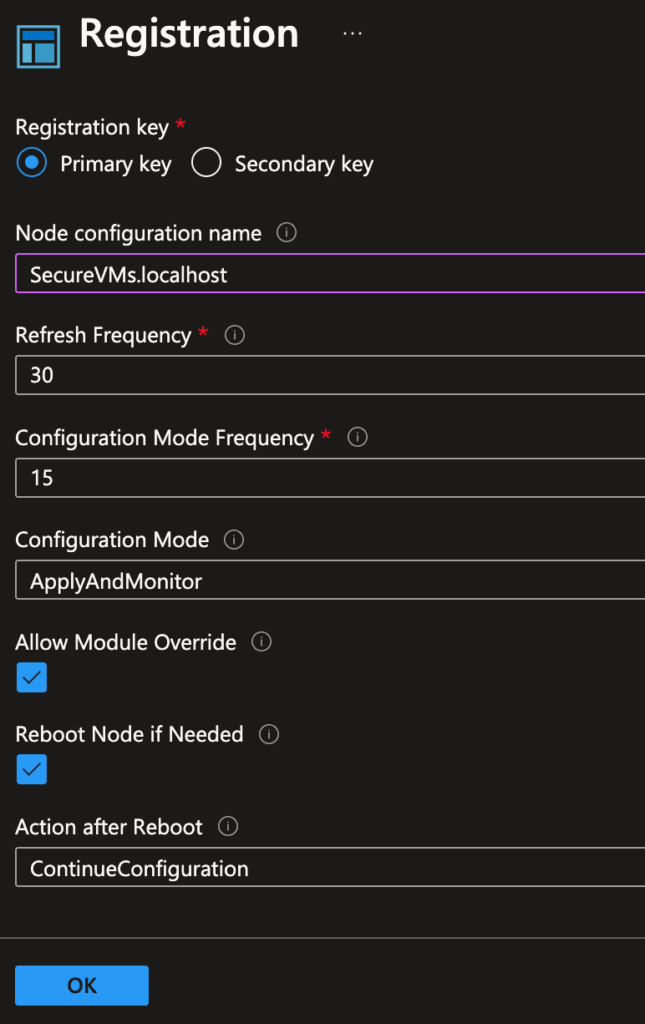
- Once compiled, go to Nodes and click Add a Node.
- Select the target Azure virtual machines and register them with the DSC configuration.

Step 4: Monitor and Enforce Compliance
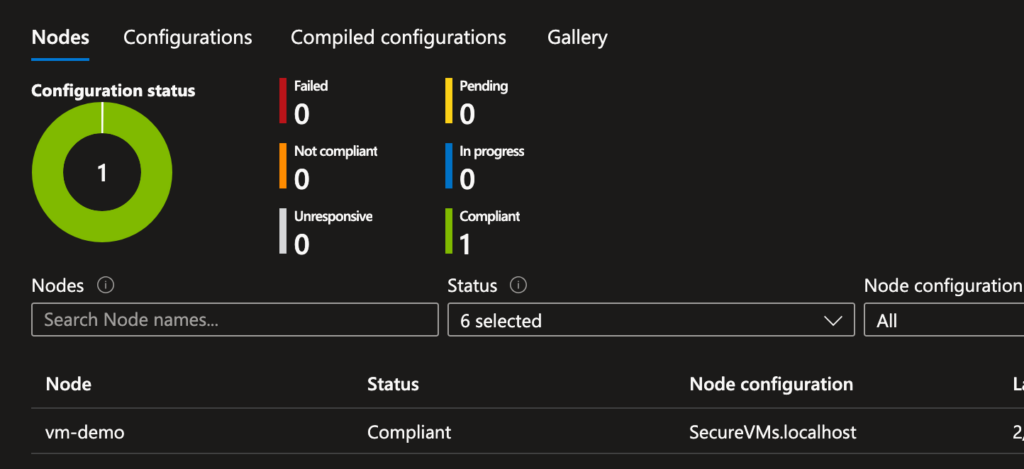
- Navigate to DSC Nodes under Azure Automation.
- Verify that the virtual machine status is Compliant.
- If any configuration drift occurs, DSC will automatically remediate the issue.
- Logs and reports can be accessed via Log Analytics and Azure Monitor.
Outcome
With Azure Automation DSC, security configurations are:
- Automatically enforced on all registered virtual machines.
- Continuously monitored to detect any drift.
- Aligned with security best practices for encryption, malware protection, and identity management.
Key Benefits of DSC for Azure Security
- Enforcement of Security Standards: Implements CIS, NIST, and Azure Security Benchmark recommendations.
- Prevention of Configuration Drift: Blocks unauthorized changes to security settings.
- Reduction of Attack Surface: Ensures firewall rules, access control, and encryption policies are applied.
- Enhanced Threat Detection: Monitors configuration changes and integrates with SIEM solutions.
Best Practices for Secure DSC Implementation
- Use Secure Modules: Ensure DSC modules come from trusted sources.
- Apply Least Privilege: Restrict permissions on DSC-managed settings.
- Integrate with Defender for Cloud: Leverage security recommendations from Defender for Cloud.
- Encrypt Configuration Data: Protect sensitive information used in DSC.
- Regularly Audit DSC Logs: Monitor for security violations and respond promptly.
Conclusion
By using Azure Automation DSC, organizations can ensure that their Azure virtual machines consistently adhere to strict security configurations. This approach automates compliance enforcement, reduces attack surfaces, and enhances overall security posture. DSC thus provides a robust solution for maintaining secure and efficient cloud environments in Azure.