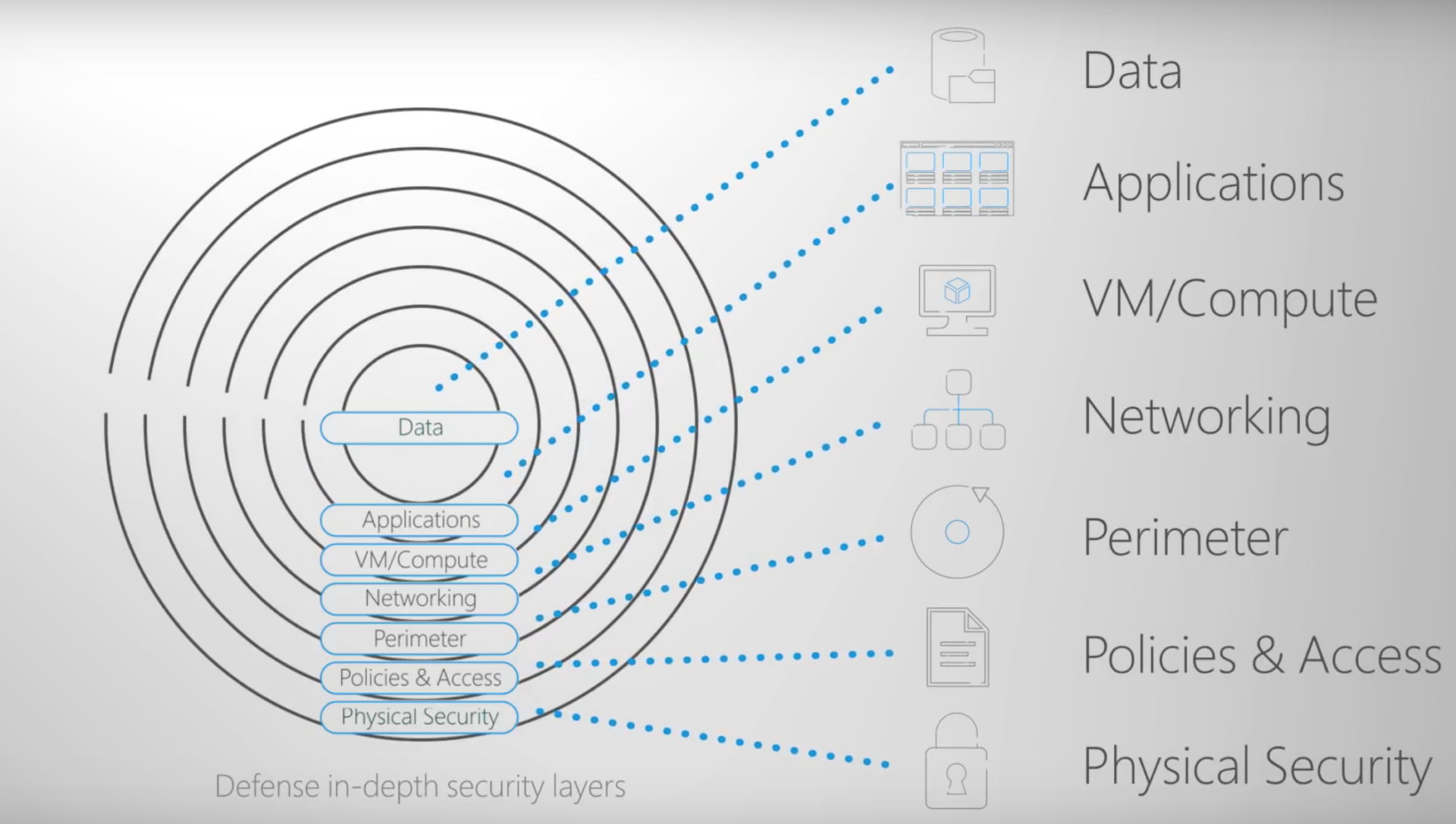
As cloud adoption grows, so does the complexity of securing environments in platforms like Microsoft Azure. Microsoft Azure offers a wealth of tools and practices to protect your resources, but ensuring comprehensive security requires a multi-layered approach known as defense in depth.Defense in depth is a security strategy that employs multiple layers of defense across various areas to protect against different types of threats. It ensures that if one security layer fails, another is ready to mitigate potential damage. In this article, we’ll explore how Azure implements defense in depth and provide actionable tips for enhancing security posture across each layer.
1. Physical Security: Securing Data Centers
Although cloud environments feel intangible, they rely on physical data centers. Microsoft Azure operates through highly secure global data centers with strict controls, including:
- 24/7 monitoring and surveillance
- Controlled access using biometric scanning and multi-factor authentication
- Redundant power supplies and cooling systems to prevent outages
Azure’s data centers meet a range of global compliance standards like ISO/IEC 27001 and SOC 2, ensuring that the infrastructure remains physically secure.
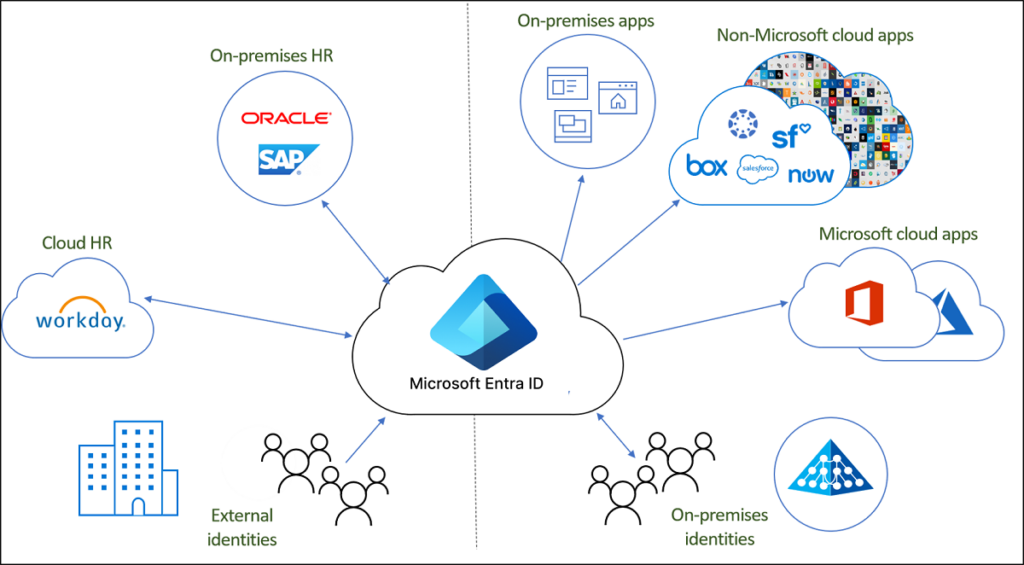
2. Identity and Access Management: Protecting User Access
The next layer focuses on managing and securing identity, which is critical as compromised credentials are often the gateway to an organization’s data.
Key Azure services that help in this area include:
- Entra ID: Centralized identity and access management that allows for single sign-on (SSO) and multi-factor authentication (MFA).
- Conditional Access Policies: Define when and where users can access resources based on factors such as device status, user roles, and locations.
- Privileged Identity Management (PIM): Limit the exposure of high-privileged roles by implementing just-in-time (JIT) access and role-based access control (RBAC).
Best Practice: Always enable MFA for all users and implement strict conditional access policies, especially for privileged accounts.
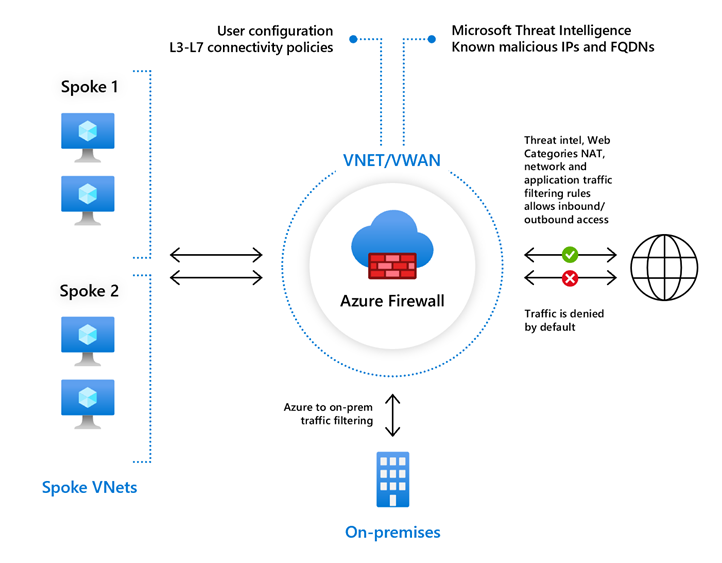
3. Perimeter Security: Strengthening Network Boundaries
At the perimeter, Azure employs several tools to limit the attack surface and safeguard against threats entering the network.
- Azure Firewall: A fully managed firewall as a service that enforces policies at the network layer. It can filter both inbound and outbound traffic across virtual networks.
- Network Security Groups (NSGs): Allow or deny traffic to Azure resources within a virtual network by creating security rules based on source/destination IP, port, and protocol.
- DDoS Protection: Azure’s DDoS Protection Service helps shield applications from distributed denial of service attacks.
Best Practice: Combine NSGs and Azure Firewall to ensure proper segmentation and enforcement of network security policies.
4. Network Security: Isolating and Securing Traffic
Even within your Azure environment, network isolation and monitoring are crucial. Techniques such as Virtual Network (VNet) segmentation can isolate workloads, and tools like Azure Bastion provide secure access to virtual machines without exposing them to the public internet.
- VNet Peering: Connect Azure VNets securely while keeping data on Microsoft’s backbone.
- Azure Private Link: Provide private connectivity to Azure services by removing the need for public IPs.
- Azure Network Watcher: Monitor network performance and gain visibility into potential issues by using tools like connection troubleshooters and NSG flow logs.
Best Practice: Avoid exposing resources directly to the internet. Leverage services like Azure Bastion for VM access, and enforce strict firewall rules for traffic management.
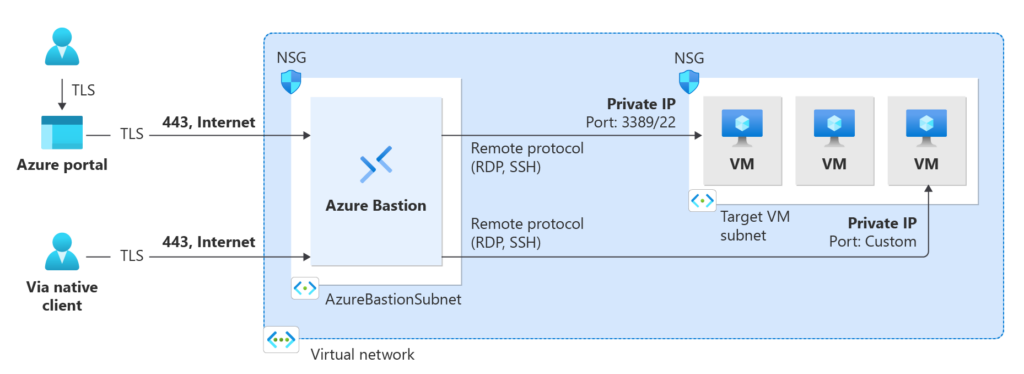
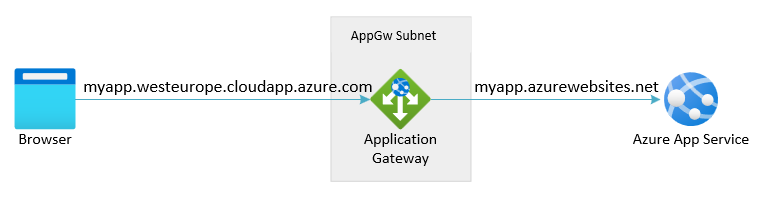
5. Application Security: Safeguarding Workloads
Application security is vital for defending Azure workloads. Here, you can take advantage of Azure-native services to protect against known vulnerabilities and exploits.
- Azure Web Application Firewall (WAF): Protects web applications from common attacks like SQL injection and cross-site scripting (XSS).
- Azure Application Gateway: Enables web application firewalling and routing across Azure environments.
- App Service Environment (ASE): Provides isolated and fully managed environments for hosting apps with enhanced security.
Best Practice: Regularly scan for vulnerabilities using tools like Defender for Cloud and ensure that WAF policies are up-to-date to mitigate web-based threats.
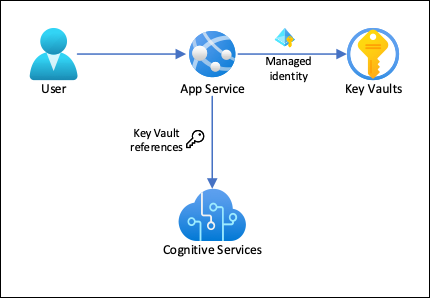
6. Data Security: Protecting Stored and In-Transit Data
Azure offers robust encryption features to protect data both at rest and in transit.
- Encryption at Rest: Azure Storage automatically encrypts data using 256-bit AES encryption.
- Encryption in Transit: Services like Azure VPN Gateway and ExpressRoute provide secure and encrypted connections between your on-premises networks and Azure.
- Azure Key Vault: Manage and store sensitive information such as encryption keys, secrets, and certificates.
Best Practice: Use Azure Key Vault to secure sensitive data, and enable encryption at both the storage and network levels.
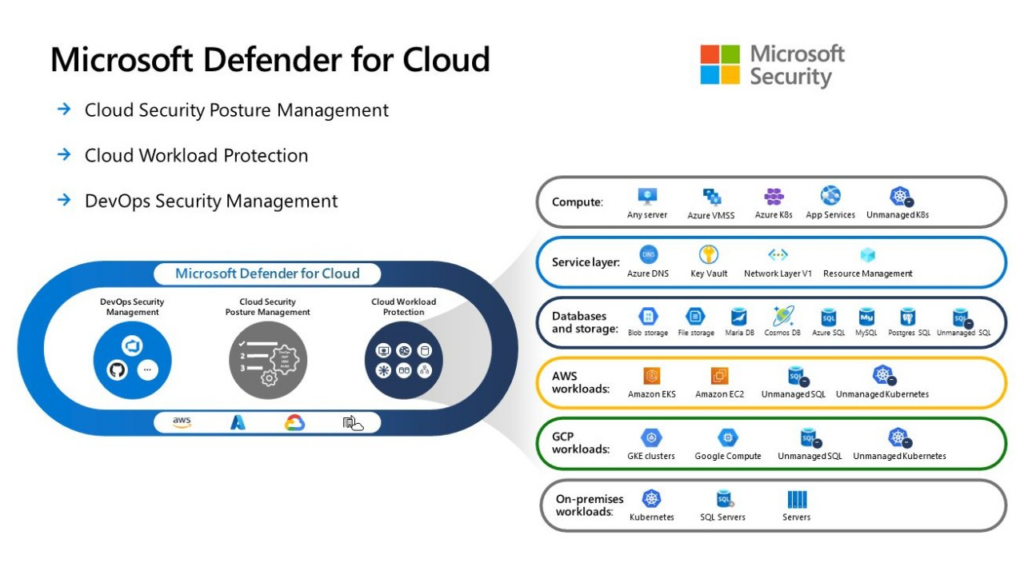
7. Monitoring and Response: Real-Time Threat Detection
Monitoring and quick response to security threats are essential parts of defense in depth. Azure offers several tools to maintain visibility over your resources and detect abnormal activities.
- Microsoft Defender for Cloud: Provides continuous monitoring, recommendations, and security alerts across your Azure, AWS, and GCP resources.
- Azure Sentinel: A cloud-native SIEM (Security Information and Event Management) solution that enables real-time threat detection and investigation through AI and automation.
Best Practice: Enable Microsoft Defender for Cloud and configure Azure Sentinel to monitor critical logs and trigger alerts on suspicious activities.
Conclusion
Microsoft Azure’s multi-layered defense-in-depth approach is designed to mitigate risks and protect cloud environments from different angles. By implementing best practices across identity, network, application, and data layers, organizations can strengthen their overall security posture. With Azure’s integrated security tools and a comprehensive defense-in-depth strategy, businesses can face the evolving threat landscape with confidence.