How Token Generation and Authentication Work?
Token generation and authentication in Entra ID involve a sophisticated process designed to secure user identities and control access to resources. Understanding this process is crucial for identifying potential vulnerabilities and implementing safeguards.
User Authentication
The process begins when a user attempts to access a resource protected by Entra ID. The user must first prove their identity, typically by providing credentials such as a username and password.
For enhanced security, Entra ID supports Multi-Factor Authentication (MFA), which requires additional verification methods such as a phone call, SMS, or an authentication app. MFA significantly reduces the risk of unauthorized access due to compromised credentials.
Entra ID also supports passwordless authentication methods like biometrics (fingerprint or facial recognition) and FIDO2 security keys, further strengthening security.
Token Issuance:
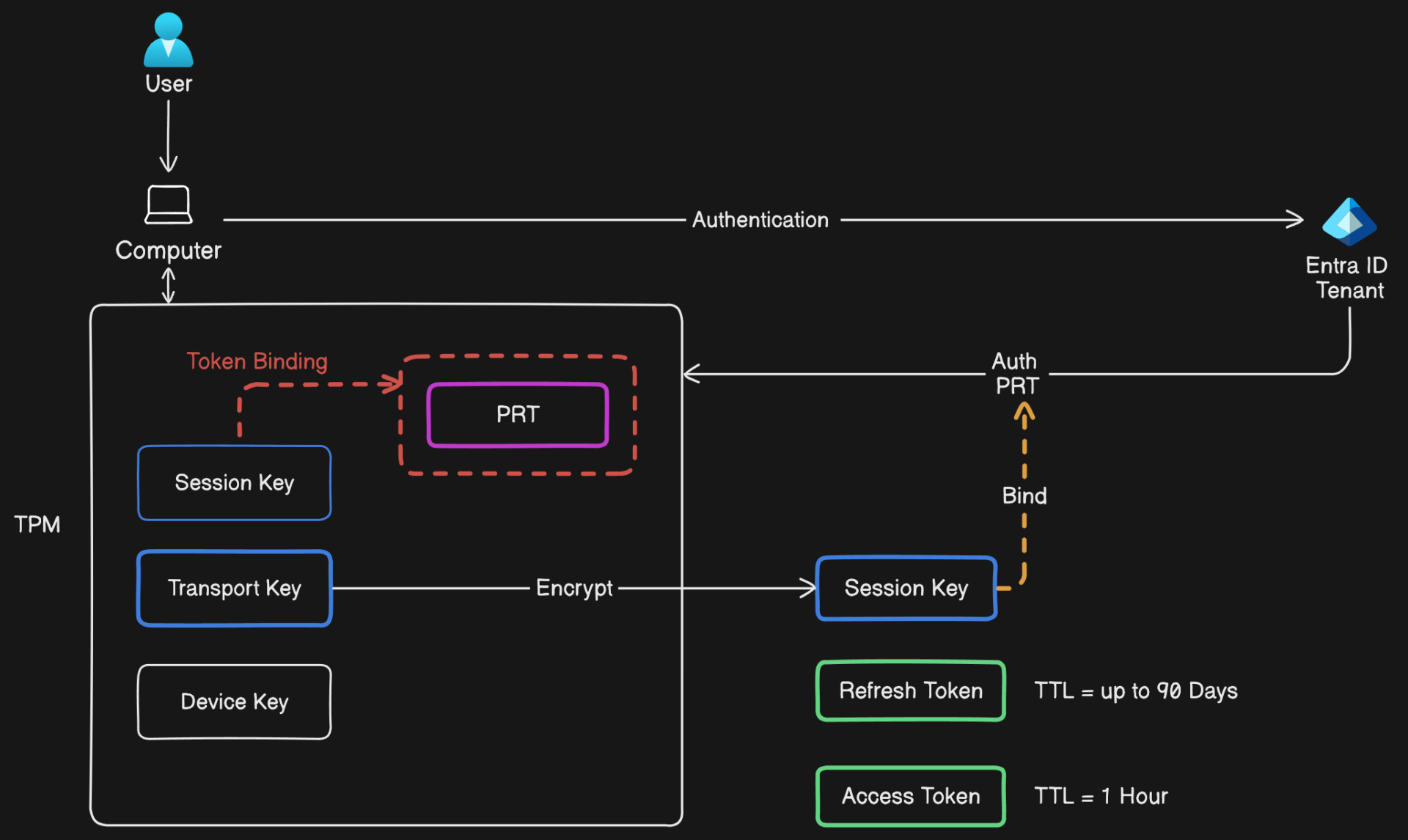
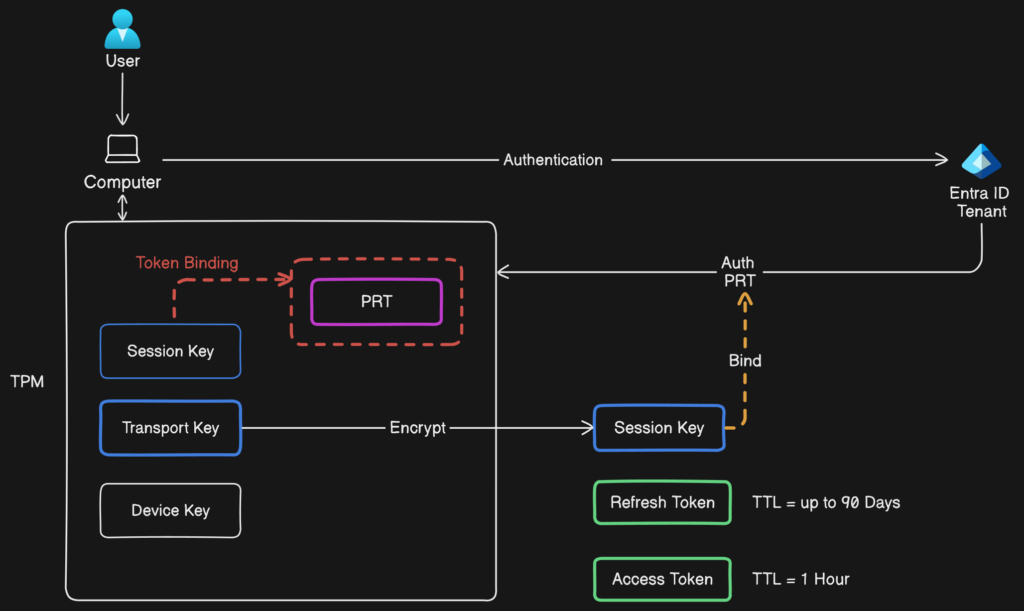
Once the user is successfully authenticated, Entra ID issues a set of tokens, including the Primary Refresh Token (PRT), Access Token, and ID Token.
- Primary Refresh Token (PRT): A key component in Entra ID’s Continuous Access Evaluation (CAE) model, the PRT is a long-lived token stored securely on the user’s device. It silently requests new Access Tokens as needed, containing claims such as the user’s identity, device ID, and additional security attributes.
- Access Token: This short-lived token, typically valid for one hour, contains claims about the user, granted scopes (permissions), and other metadata required for accessing specific resources.
- ID Token: Primarily used by applications to obtain basic information about the authenticated user, such as their username and email address. The ID Token is crucial for establishing the user’s identity within the application, though it is not typically involved in resource access.
Session Keys and Secure Storage
Along with the PRT, Entra ID generates a Session Key, securely stored within the device’s Trusted Platform Module (TPM) or an equivalent hardware security module. The TPM ensures that sensitive data like the Session Key cannot be easily extracted or tampered with by malware or attackers. If the device lacks TPM support, Entra ID employs software-based encryption mechanisms, although these are considered less secure.
Token Types and Lifetimes
Entra ID issues different types of tokens, each with distinct purposes and lifetimes:
- Access Tokens: Short-lived tokens used for accessing resources such as APIs, files, or other services. Their short lifespan helps minimize the impact if a token is compromised.
- Refresh Tokens: Long-lived tokens used to request new Access Tokens without requiring the user to re-authenticate, generally valid for up to 90 days.
- Primary Refresh Token (PRT): Valid for 14 days, the PRT is essential for seamless access across sessions and resources, with silent renewal if the user is active.
Entra ID’s token expiration policies are designed to balance security with user convenience. By using short-lived Access Tokens and leveraging PRT and Refresh Tokens, Entra ID limits the potential damage if a token is stolen.
Token Encryption and Validation
All tokens issued by Entra ID are signed using asymmetric keys, ensuring that they cannot be tampered with or forged. The signature is validated by the resource server or API when the token is presented, confirming its integrity and authenticity.
Tokens are also encrypted to protect sensitive information if intercepted during transmission. Entra ID supports Conditional Access policies that dynamically evaluate access requests based on signals such as user location, device compliance, and risk level, potentially enforcing additional authentication or denying access even if the token is valid.
Continuous Access Evaluation (CAE):
Entra ID leverages Continuous Access Evaluation (CAE) to further enhance security. CAE allows for real-time policy enforcement and token revocation. If a user’s risk level changes or anomalous activity is detected, Entra ID can immediately invalidate tokens, forcing re-authentication to prevent unauthorized access. CAE is particularly effective when a token has been compromised but is still within its validity period, proactively mitigating the risk.
Token Theft
Understanding Tokens and Their Value:
In Entra ID, tokens are essential for granting access to resources without repeatedly asking users to re-enter credentials. However, this convenience makes tokens a prime target for attackers. If an attacker obtains a valid token, they can impersonate the user and access resources without detection.
Common Methods of Token Theft
- Phishing Attacks: Attackers trick users into visiting malicious websites resembling legitimate login pages. Upon entering credentials, attackers capture them and obtain tokens from Entra ID. In some cases, attackers can directly steal tokens if the user is already authenticated.
- Man-in-the-Middle (MitM) Attacks: In MitM attacks, attackers intercept communications between a user and a service. If these communications are not properly encrypted, attackers can capture tokens in transit.
- Malware: Malware can be designed to extract tokens from a user’s device, using methods like keyloggers or browser exploits. More sophisticated malware may target the device’s memory or TPM where session keys are stored.
- Session Hijacking: Session hijacking occurs when an attacker takes control of a user’s active session, often by stealing a session cookie containing a token. This can happen if the user’s device is compromised or connected to an insecure network.
- Token Replay Attacks: In a replay attack, an attacker captures a token and reuses it to gain unauthorized access to resources.
Targeting Specific Token Types
- Access Tokens: These tokens provide direct access to APIs, services, and data. Although short-lived, they can still cause significant harm if stolen and used quickly.
- Refresh Tokens: With a longer lifespan, refresh tokens are even more valuable to attackers, allowing them to maintain access over an extended period.
- Primary Refresh Token (PRT): The PRT is critical in the Entra ID ecosystem. If compromised, it allows attackers to continuously request new access and refresh tokens without needing the user’s credentials.
Token Binding
Token Binding is a security mechanism designed to enhance the security of token-based authentication systems by binding tokens to a specific client or device. This process mitigates risks associated with token theft and replay attacks.
- Cryptographic Binding: Token Binding uses cryptographic keys to link a token to a specific client, making it unusable by attackers who lack the corresponding private key.
- Sender Constraining: Ensures that the token is only valid when presented by the client that originally received it.
- Enhanced Security: Binding tokens to specific devices or sessions significantly reduces the risk of token misuse, improving overall security in token-based authentication systems.
Primary Refresh Token (PRT)
The Primary Refresh Token (PRT) is a critical component of Microsoft Entra ID’s authentication framework, particularly for Windows 10 and newer devices. It facilitates single sign-on (SSO) experiences across applications while maintaining security.
- Issuance: A PRT is issued when a user successfully authenticates on a registered device. It is tied to the device and used to obtain new access tokens without requiring the user to re-authenticate.
- Claims and Security: The PRT contains various claims, including a device ID and a session key, which is securely encrypted and acts as proof of possession.
- Lifetime and Renewal: A PRT typically has a 14-day validity period but can be continuously renewed as long as the user actively uses the device.
- Protection Mechanisms: PRTs are protected by binding them to the device on which they were issued, enforced through hardware security features like the Trusted Platform Module (TPM).
How to protect against token theft
To enable token protection, organizations can configure Conditional Access policies with key features:
- Require Token Protection for Sign-In Sessions: Mandating that all sign-in sessions must use tokens bound to the authenticated device ensures that only legitimate sessions can access protected resources.
More information about this can be found in the documentation link:
https://learn.microsoft.com/en-us/entra/identity/conditional-access/concept-token-protection
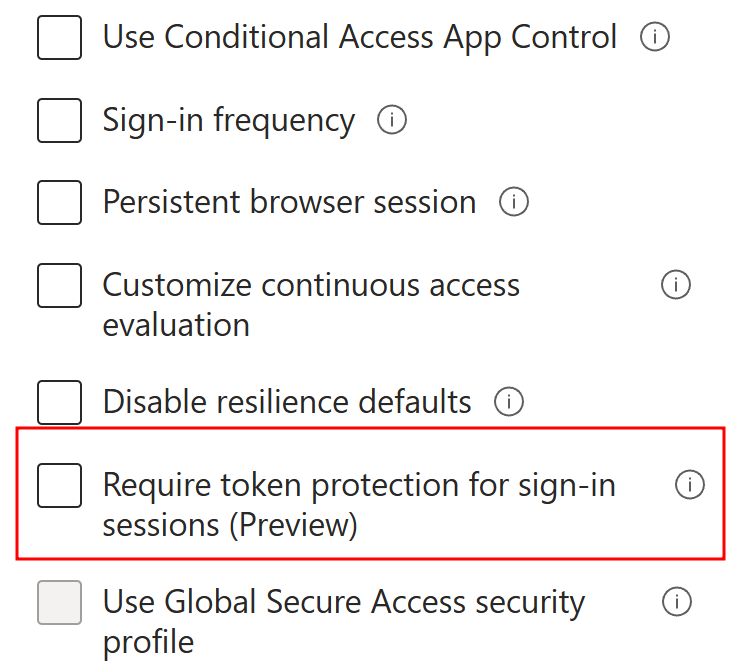
- Device Compliance: Policies can require that devices used for accessing resources meet specific compliance criteria, such as being registered with Azure Active Directory (AAD) and having necessary security configurations in place.
- Supported Resources: Token protection is initially applied to high-value resources such as Microsoft Exchange and SharePoint, with plans to extend protection to other applications and services.
- Proof-of-Possession Mechanism: When accessing a resource, the system checks for proof of possession, verifying that the client can access a private key stored on the device.
Conclusion
Token security is vital in modern authentication, particularly within Entra ID. By understanding how tokens are generated and protected, organizations can better defend against threats. Entra ID’s advanced mechanisms, such as the Primary Refresh Token (PRT) and Continuous Access Evaluation (CAE), provide secure access but also introduce vulnerabilities that attackers exploit. Implementing strong protection strategies like Conditional Access policies and Token Binding can significantly enhance security. As reliance on cloud services increases, mitigating token theft risks remains essential. Proactive measures will ensure tokens effectively safeguard user identities and access to critical resources.